A Brief History of Game Cheating

Over the short span of video game cheating, both cheaters and game developers have evolved in many ways; this includes everything from modification of important game variables (like health) by using tools like Cheat Engine. In addition, game botting impacts both game and real-life economies. However, using modern-day anti-cheat methods is also not without danger, as modern protection tools run on the kernel level and can be abused for malicious impact on the system. For example, a local privilege escalation exploit has recently been found in a popular anti-cheat solution, enabling ransomware actors to disable anti-virus solutions on the system.
In this post, we will go over the history of cheats and their evolution; for each one, we will present how they work with examples and share some methods game developers employ to protect their games against those cheats.
On that note, we need to mention what this post is not:
- We will not deep dive into how to implement cheats.
- We do not encourage anyone to cheat in games, especially multiplayer games, as you harm yourself and others.
The Endless Game of Cat and Mouse
I vividly remember the day I discovered video game cheating, a moment that likely steered me towards cybersecurity later in life. As a child in the early 2000s, I was fortunate to have access to my school’s computer lab during recess. During one such recess, I was playing Counter-Strike with my classmates. Accidentally, I pressed the ~ key, which opened the developer console and started my path in video game cheats. By the end of that session, I had disabled gravity and discovered “god mode,” which allowed me to turn a routine game match into an astronaut simulation where I could not get killed by anyone. It’s safe to say my classmates didn’t have much fun that day.
In this day and age, the dangers of cheating are far greater than having our fellow classmates angry at us. Cheating usually results in banned accounts and, sometimes, with a cherry on top, malware running on our computers, as cheats commonly contain malicious software built into them.
It’s in our nature to never trust something free, and this makes sense with cheats as they are known to be riddled with malware. Nonetheless, there’s a preconceived notion that paying for the cheat is safer. Presumably, this is because we’ve already given money to the developer and thus mitigated any thought of embedding malware into the cheat. Sadly, as we will show in a soon-to-be-released deep dive, this is far from the truth.
Lvl 0: Built-in Cheats
This is level zero, and at this level, we will encounter tools that the developers left behind, usually meant to test the various game functionalities. A great example of this would be the plethora of secret codes in The Sims 2, like “Motherlode” that gave you 50,000 of the game’s currency, or “CPKTNWT” in Grand Theft Auto: San Andreas (Figure 1) that exploded all the cars around the player when typed into the game as depicted in the meme below (tip: don’t do this to your friends as this may or may not result in physical retaliation).

Figure 1: GTA: San Andreas cheat code in action
Lvl 1: Local File Modification
Going up a notch, local file modification is usually an effective cheating method in both single-player and multiplayer games, but luckily, it’s relatively simple to protect against in multiplayer games, as we will soon discover.
In single-player games, we run all the software on our local CPU. Furthermore, we rely on locally stored configuration files and game save data. The nature of locally stored data is that there are almost no ways to detect a modification to those files through an external editor.
For example, in Terraria, a game about exploration and gradual progression, there are several tools to edit the contents of the player’s inventory and their stats by modifying the save file, allowing us to give out any item in the game with a click of a button.
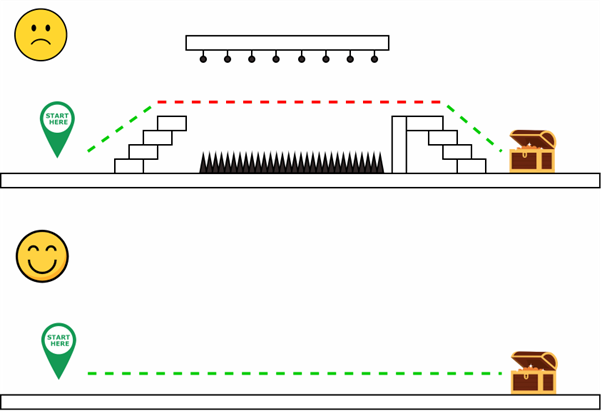
Figure 2: Simplified Diagram of World of Warcraft 2006 Dungeon Bypass
In multiplayer games, this tactic is very effective in cases where the server fails to validate the information sent by the client.
A very famous example is from World of Warcraft around the year 2006. A clan called Overrated found a method to cut down the time needed to complete a long and cumbersome encounter by simply removing most of the map, as illustrated above in Figure 2. This allowed them to go directly to the end boss, hiding data from the client that enabled them to skip most of the difficult and fatiguing content.
An easy way to combat this type of cheating is through verification. Ideally, this should start from a signed executable that is automatically verified based on its signature, followed by a check of the integrity of local files. Complementing this with server-side verification of client actions is also highly recommended. For instance, a server can check if a player walked through a wall or picked up an item off the floor from 12 kilometers away.
Lvl 2: External Memory Modification
At this level, we explore modifying games while they’re running. More specifically, we will examine how externally editing game variables can be used to gain an unfair advantage.
One of the early and famous examples of external memory modification is the “unlimited health” cheat in Diablo II. Here, players made themselves invincible by freezing their health value to stay the same no matter what amount of damage they had taken.
Cheat Engine is the most popular tool for locating and modifying game variables during runtime. It works by identifying memory addresses where these variables are stored by searching the whole process for a specific value. Though this initially produces a long list of addresses containing unrelated variables, a simple trick can narrow down the results. Take the Diablo II cheat as an example:
Step 1 – Do an initial scan over the process memory, searching for our current health value. This will return a long list of all the memory addresses containing the same value we are looking for.
Step 2 – Modify our current health by taking a small amount of damage or healing; we will utilize Cheat Engine’s variable tracking feature to filter out variables that don’t change, like our health.
Step 3 – Do a second scan with the new value of our health. This should reduce the list by a significant amount. If the list is still long, we repeat Steps 2 and 3 until we narrow it down to have only our health variable.
Step 4 – Modify or lock the variable as needed.
Like in level one, this method works well in single-player games as they usually don’t have protections against changes to the game’s memory or checks on the server side. But developers can still fight these modifications. An interesting method is to store values more complexly, like storing the health as health + 12, which makes it harder to find and change the value.
Another method used mainly in multi-player games is to protect the game with an off-the-shelf anti-cheat solution. They check all access attempts to the game’s memory block, including prohibited ones. These programs are improving every day, and many game developers use these solutions instead of making them, thus enabling them to focus on the game instead of anti-cheating features.
Lvl 3: Botting
Unlike previous levels, botting usually doesn’t change how the game behaves but automates it. It’s a widespread method to gain an unfair advantage and is even used to gain real-life currency in games with a player-driven economy. Usually, players avoid doing mundane mechanics that require repetitive and simple actions; in some cases, those actions provide goods that players would buy instead of doing the mechanic. This opens a market for providing those kinds of goods for a nice amount of in-game currency, and cheaters take advantage of that.

Figure 3: A group of bots mining
One of the most notable examples I have personally encountered is in the game RuneScape, a story-rich game with around 29 different skills. Many of them are locked behind the game’s membership system, which either costs real-world money or can be gained through in-game items called bonds, which give you two weeks of premium membership essentially for “free.”
Bonds are a traded commodity, meaning that any player can collect enough in-game currency and buy it. Based on our calculations, a free-to-play player who wants to gain enough currency must work hard and usually do very repetitive tasks for upwards of 10 hours to earn enough to buy a single bond, thus the high motivation for botting.
To implement botting, users need to download an external tool that automates the game by simulating the player actions with mouse and keyboard input or through an API to talk with the game servers directly.
Regardless of the bot implementation method, botting is always dangerous. First, anti-bot measures are becoming increasingly smarter and better as they find hidden patterns that indicate that we are using external software. This puts our accounts in danger if we get caught using software to automate them. Second, botting requires us to run an unknown executable on our computer, potentially making us run a malicious piece of software and getting all our information stolen.
Lvl 4: Hooks
At this level, we delve into the complexity of video game cheating through hooking. Cheats at this stage can significantly alter a game’s internal workings or exploit hidden information to provide players with an unfair advantage.
Let’s examine two common types of cheats:
1. Aim assist
2. Wallhack
Aim assist is a popular cheat that modifies the game’s aiming mechanics, making it easier for players to hit their targets more accurately and consistently. This can drastically change the outcome of multiplayer matches, as skilled players with aim assist have an unfair edge over others. A cheater can bypass the intended aiming logic and manipulate it to always hit the target by hooking into the game’s aiming and shooting functions.
Wallhack is another common cheating method involving exploiting hidden information in a game to gain visibility through walls or other obstacles. This cheat can provide players with crucial information about their opponents’ positions, allowing them to make strategic decisions and execute surprise attacks. By hooking into the game’s rendering functions, a cheater can also manipulate the data being displayed and overlay the location of enemies even through walls, gaining an unfair advantage.
It’s important to note that using such cheats in multiplayer games not only disrupts fair play but also violates the terms of service set forth by game developers. Most modern games employ anti-cheat solutions like EasyAntiCheat to prevent such activities, which monitor access attempts to the game’s memory and only allow authorized changes. These programs continuously evolve, making it increasingly difficult for cheaters to bypass their protections.
This approach to anti-cheating has been found highly effective in conjunction with a community-lead review system like the one in Counter-Strike: Global Offensive, where veteran players gain access to suspected cheater recordings and share their observations. This leads to both greater awareness for players and higher-quality detections from anti-cheat mechanics in the game.
Lvl 5: Direct Memory Access
Until now, anti-cheat solutions have been a catchall solution for cheating through memory modification and access. But what if we told you that even the best anti-cheating solutions, like the notorious Vanguard by Riot Games, can be bypassed by not running the cheat logic on our computer at all?
Direct Memory Access (DMA) requires access to the game memory to function. Unlike the methods mentioned earlier, this is done through a custom hardware component that cheaters buy and install on their computers. This allows a second computer to interface with the computer’s main memory (RAM) and directly access the game memory.
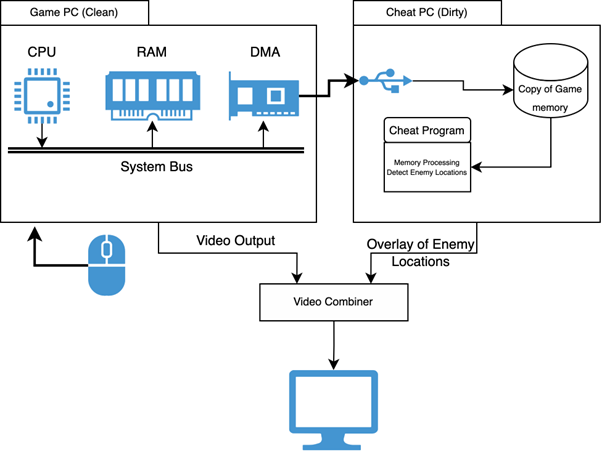
Figure 4: DMA flow with video overlay
Usually, this hardware is expensive and requires additional hardware to complement the cheat. For example, suppose we want to display the enemy location on the screen as depicted in Figure 4. In that case, we will need a device that overlaps two video outputs, as we can’t risk displaying any cheat-related information on the main computer running the game.
But why does DMA succeed at bypassing strong anti-cheat solutions like Vanguard?
It all stems from those solutions running at the kernel level, protecting against access to the protected memory from programs running on the current computer by forcing them to go through their detection logic on every memory access. However, DMA works differently, using a custom PCIe controller to directly access the memory without going through the CPU, which is the anti-cheat solution.
Over the years, anti-cheat solutions have found methods to detect DMA devices by scanning all connected devices and checking their unique identifier. However, several DMA devices can also bypass this by spoofing the identifier and making it seen as a USB controller or an additional graphics card.
But at What Cost?
There are two kinds of cheaters: the everyday average player who wants to gain a slight edge, usually for fun or because of a lack of skill. The second kind is a malicious cheater who gains something from cheating; some do this for publicity, and some even to win tournaments and earn money.
The latter type has the time, money and usually the knowledge to create their own cheats. This kind of cheater forces the gaming industry to work on anti-cheating solutions, as cheaters of this magnitude make the games appear in a negative light.
While game developers work around the clock to detect and block cheaters, this has affected legitimate players in ways that aren’t always as obvious as they might seem initially.
First, the added time and effort needed to add anti-cheat solutions costs money, which is then reflected in the game’s price and is taken from us, the consumers. Second, having a strong anti-cheat solution that runs on the kernel level is a ticking time bomb; as those solutions run at the system level, they are a prime target for hackers to exploit.
This has happened in the past in games like Genshin Impact containing CVE-2020-36603, where a local privilege escalation exploit has been found in their anti-cheat solution, resulting in ransomware being able to disable anti-virus solutions.
Recently, the game APEX Legends made headlines when several high-profile players were hacked during a tournament and seemingly remotely controlled by the attacker through the game servers. This disrupted a costly event and damaged the game and the company’s public image.
While the community immediately suspected the anti-cheat solution, which is a must for a competitive game like APEX Legends, the actual exploit was in the game server and potentially their game clients, such as Respawn. The company behind APEX has released a security fix.
If there’s one thing we want you to take home from this post, it’s that the endless cat-and-mouse game is here to stay with us for the near future. We already see that anti-cheat solutions are tackling the problem of DMA-based cheats, and we are sure that the cheaters have more tricks up their sleeves. Ultimately, consumers money will fund all this back-and-forth, whether we want it or not.
There are real dangers when it comes to game cheating. In the next post, we’ll dive into a situation in which a developer sold his cheat for a large amount of money and stole information from his clients, raising some eyebrows and forcing us to ask – can premium cheats even be trusted?
David El is a malware researcher at CyberArk Labs.