Why ITDR Matters for Your Enterprise’s Identity Security

You may not recognize the term Identity Threat Detection and Response (ITDR), but this emerging security discipline aims to address an all-too-familiar challenge: managing and securing the massive number of identities – human and machine – across the enterprise.
What is ITDR?
To understand ITDR, it’s helpful to first define what ITDR is not. ITDR isn’t a silver-bullet cybersecurity solution that offers complete identity protection from security breaches; there is no such thing. It isn’t a group of identity and access management (IAM) prevention controls. ITDR coverage isn’t limited to a specific area such as the endpoint, nor is ITDR meant to detect a broad swath of cyber threats.
Instead, ITDR is a system of structured processes, cross-functional team collaboration and threat intelligence and behavior analysis tools working in concert to protect the identity infrastructure itself. ITDR adds a defense-in-depth layer to preventive identity security defenses – such as privileged access management (PAM), multi-factor authentication (MFA) and identity governance and administration (IGA) – to rapidly remediate identity-centric attacks. ITDR supports Zero Trust by employing detection and response mechanisms to identify potential threats, examine any suspicious activity during and after the authentication and authorization process and take the appropriate countermeasures through security orchestration and response.
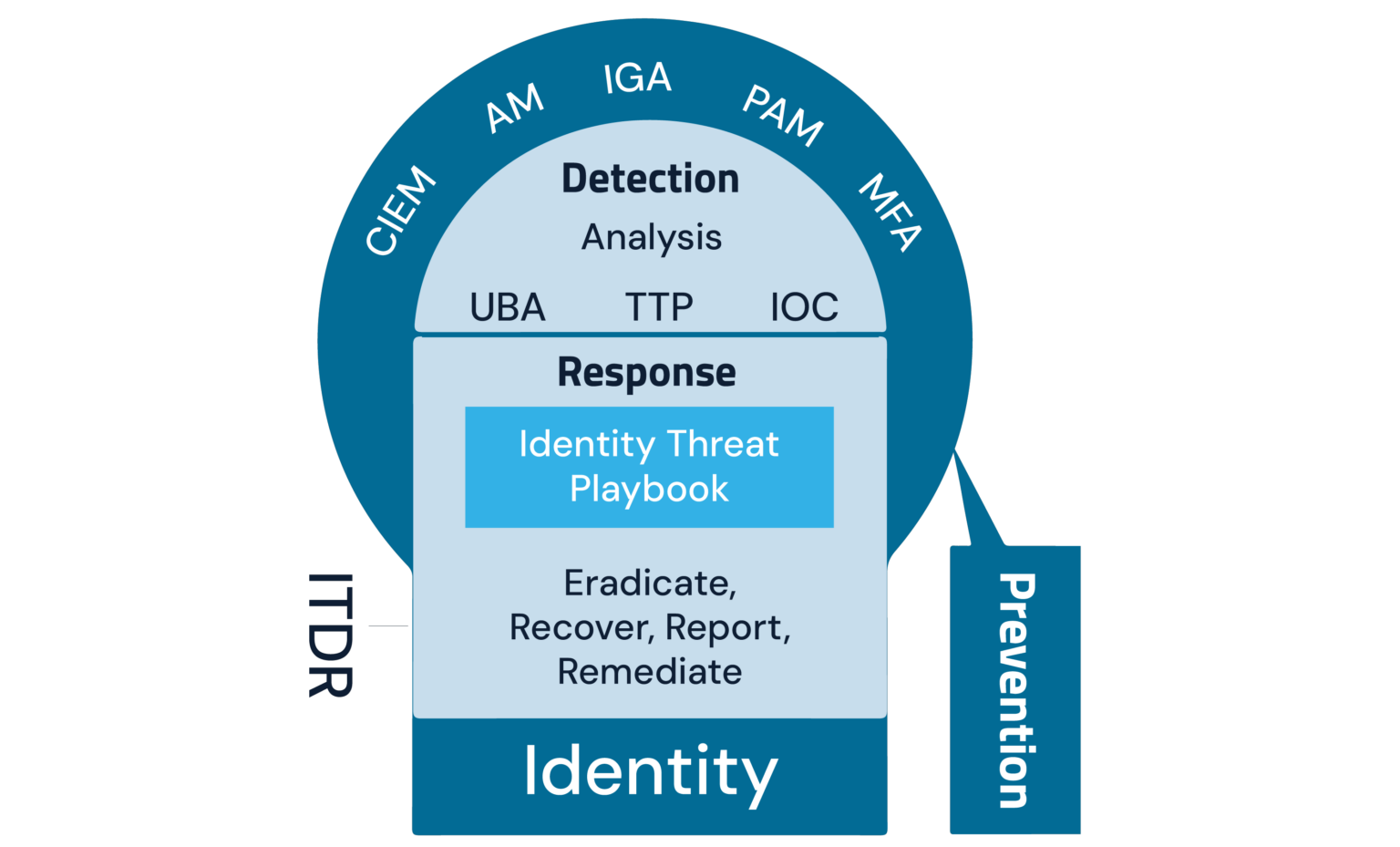
Why Does ITDR Matter?
In this ITDR crash course, you’ll explore eight adoption drivers that demonstrate why ITDR matters and how it fits into the broader cybersecurity picture.
- If you can’t trust the identity or identity source, you can’t trust any security control. Threats that target identity infrastructures can compromise an entire environment – underscoring the need for ITDR. Similarly, the infamous SolarWinds software supply chain breach showed that if an attacker can successfully infiltrate systems with privileged access to high-value systems and data, they could potentially impersonate any human or machine identity, pass any authentication/ authorization challenge and other entitlement controls and rapidly escalate privileges to reach their goal. To counter these sophisticated threats, organizations must implement strong controls to block and contain attacks from the start. But assuming that your environment has already been breached also means adopting ways to rapidly identify and analyze post-authentication red flags, then take appropriate countermeasures to safeguard the trustworthiness of the identity infrastructure through security orchestration and response.
- Identities are everywhere. IT security professionals understand that stolen, abused or misused identities – whether privileged or not – are a gateway to sensitive information. According to the CyberArk 2023 Identity Security Threat Landscape report, nearly all IT security professionals (99%) anticipate an identity-related compromise this year. Unaddressed identity risks due to economic slowdown, an expected 240% growth in human and machine identities, increased cloud migration and accelerating attacker innovation are all contributing factors.
- In the security operations center (SOC), most threat detection tools monitor a broader scope to cover many use cases. HelpNetSecurity reports that on any given day, the SOC team receives about 4,484 threat alerts from these systems and spends nearly three hours on manual triage. Overwhelmed by false positives coming from disjointed tools, 97% of SOC analysts worry about missing a relevant security event. According to the 2023 Verizon DBIR, 74% of security breaches involve the human element (i.e., social engineering attacks, errors and misuse), so there’s a good chance those missed events tie back to identity. Unlike most SOC tools, identity-based threat detection tools specifically aim to protect the identity infrastructure to maintain the trust of the identity database.
- Individual user access control often ends after the authentication/authorization process. Most of today’s threat detection and response tools focus on very specific threats. For example, EDR tools focus on the endpoint and lack visibility and control beyond that (e.g., cloud-based applications and infrastructure and local datacenters are not under the EDR coverage). Controlling and monitoring user access to different environments requires a more centralized and granular solution that focuses on the identity infrastructure. With this approach, organizations can continue to monitor the user session – regardless of the environment – after the authentication and authorization process. This allows them to respond to threats quickly and reduce possible breaches to identity infrastructure.
- Identity security isn’t linear. Since identity is the perimeter, a security continuum – not a straight line – is the only way to continuously track trust. With ITDR, policy-based threat prevention, detection and response exist in a continuous feedback loop, constantly learning from – and acting upon – identity threat insights. A centralized threat analysis engine automatically detects anomalous behavior that, on its own or in combination with privileged access misuse, could be a potential threat, along with risky access to both business applications and privileged accounts. The engine also tracks the entire chain of events leading up to these suspicious actions to streamline investigations and create clear audit trails.
- Innovation can’t wait. Adaptive authentication and continuous threat monitoring mechanisms look at user behavior history and context to discern typical activities from risky ones. When they detect risky behavior (e.g., connection via a new IP address or OS, multiple failed logins or suspected credential theft), they can automatically move the user into a “risky user group,” update the MFA policy in real time (e.g., requiring more difficult factors like number-matching challenges) and temporarily limit or revoke access. Meanwhile, actionable identity-based analytics strengthen the broader cybersecurity product stack and deepen the enterprise’s overall threat intelligence capability.
- Teamwork makes the dream work. Preventing attacks requires skilled security analysts with specialized knowledge and cloud adds another complexity factor. But cybersecurity shortages make this difficult: more than four out of five companies say they have fewer than five security analysts or don’t have enough analysts to run the SOC, reveals a Censuswide study. Under-staffed SOC teams are forced to act broadly, making rapid decisions based on experience and information at hand. These professionals aren’t deeply entrenched in identity access management (IAM), which is usually a separate function in the organization. ITDR challenges this siloed model by synchronizing identity data and unifying cross-functional security teams to expand the SOC. This isn’t a shift that happens overnight, but organizations that prioritize it can dramatically enhance identity protection and bridge knowledge gaps, while creating a centralized, end-to-end threat detection and response flow in the closest real-time way possible.
ITDR Supports Zero Trust and Enhances Cyber Resilience
Changes in the digital environment have upended conventional thinking and positioned identity in cybersecurity’s center. And recent attacks on identity infrastructure underscore the need for a Zero Trust model involving least privilege enforcement and continuous threat detection for every identity across its lifecycle. This is the only way to truly ensure that only the right users access only the right resources at only the right times and for only the right reasons.
ITDR supports Zero Trust by continuously monitoring threats and automatically responding to attacks to help businesses keep their identity infrastructures secure. Now is the time to dig deeper into this critical security discipline and discover the benefits of implementing ITDR as part of a holistic identity security approach.
Claudio Neiva is CyberArk’s Field Technology Director (LATAM), PAM and Identity Security. For best practices and advice to help you plan your Zero Trust approach within your organization, check out Neiva’s new whitepaper, “Guiding Your Leadership Team Through the Zero Trust Mindset.“