How to Map Identity Security Maturity and Elevate Your Strategy
The ultimate goal of Identity Security is to provide secure access to every identity for any resource or environment, from any location, using any device. Yet ever-evolving technology and dynamic threats can make executing a comprehensive Identity Security program a complex undertaking. According to the new Enterprise Strategy Group (ESG) research report “The Holistic Identity Security Maturity Model,” most organizations (42%) are still in the early days of their Identity Security journeys. Understanding your business’s current Identity Security maturity in relation to its ideal state is vital because, in the words of Henry Kissinger, “If you do not know where you are going, every road will get you nowhere.”
So, where do you start? What assessment factors matter most? How do you stack up against industry peers and track improvement over time? To help eliminate some of this guesswork, ESG created a data-driven Identity Security Maturity Model that measures maturity levels across four distinct tenants. This model draws on insights from 1,500 global cybersecurity professionals responsible for securing identities in multi-cloud IT environments.
Prescriptive guidance is also found in the CyberArk Blueprint for Identity Security Success, a vendor-agnostic framework for developing a successful Identity Security program. The Blueprint is based on decades of experience and lessons learned from helping more than 8,000 global organizations secure their identities and protect what matters most.
Two Critical Identity Security Program Assessment Factors
As your organization thinks about building its Identity Security program, there are two fundamental factors to consider in tandem: Capability breadth and deployment depth.
The Identity Security Maturity Model describes the breadth of capabilities across tools, integrations, automation and continuous threat detection and response (CTD&R). These are capabilities and integrations your organization should strive to deliver to mitigate Identity Security risk. That guidance is supplemented by the CyberArk Blueprint, which not only considers capability breadth but also deployment depth by aligning capabilities to specific resources and environments requiring Identity Security controls.
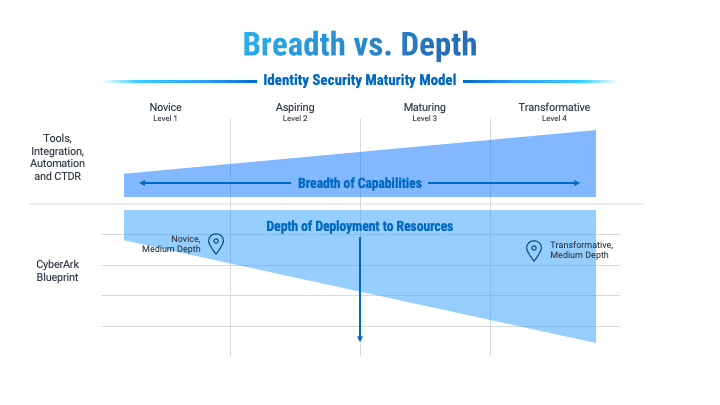
Figure 1: Identity Security Breadth and Depth Matrix
While you may understand your organization’s capability breadth, it does not explicitly correlate to the depth in which those capabilities have been implemented across your environment. For this reason, it’s essential to consider the Identity Security Maturity Model and the CyberArk Blueprint together as you chart your course.
This is illustrated in the above diagram. While the Transformative organization may be more capable than the Novice, that doesn’t necessarily mean it has implemented the right capabilities across the right identities and resources or mitigated the most prevalent Identity Security threats by risk priority.
Maximizing Your Capabilities: Guidance for Novice Organizations
If you’ve assessed your organization as “Novice,” you’re not alone: 42% of global organizations operate at this capability maturity level today.
We’ve aligned ESG’s model with our proven CyberArk Blueprint framework to help you measure the breadth and depth of your Identity Security program and determine pragmatic steps to uplevel your strategy. Your dual aim should be advancing your position in the Identity Security Maturity Model while addressing security deficiencies in risk-based phases to go deeper with the CyberArk Blueprint.
Below, we’ll demonstrate how a Maturity Level 1: Novice organization can use these combined insights to maximize Identity Security capabilities and outcomes.
Snapshot of a Novice Organization
While 38% of Novice organizations believe they’ve made correct identity-related decisions, most organizations at this level have yet to invest in foundational Identity Security tools and lag in integrating and automating tools they do have in their environments. Existing controls tend to focus heavily on human identities, leaving third-party and non-human identities unmanaged. Generally, these organizations lack the confidence to mitigate identity-related risks promptly and are slow to respond to audit requests.
There is a clear gap between investment and outcomes at this level: 32% of Novice organizations have suffered two or more successful identity-related cyberattacks compared to just seven percent of the most mature organizations – those categorized as Transformative. Many of these attacks stem from credential compromise and malware. Novice organizations point to fragmentation, insufficient staffing and budget constraints as major roadblocks yet continue to forge ahead with cloud adoption that can significantly expand the attack surface.
Novice Blueprint Focus: Secure High-Value Targets for Rapid Risk Mitigation
Without proper Identity Security controls in place, malicious actors can easily steal credentials to exploit identities, move laterally and vertically throughout the environment, and ultimately escalate and abuse privileges to achieve their goals. This attack chain is at the center of all identity attacks.
Fortunately, Novice organizations can quickly address their greatest liabilities by focusing on highly privileged identities, which attackers often exploit to take control of an environment. These identities may have entitlements such as cloud admin, domain admin, hypervisor admin or Windows server admin. The personas who consume these privileges are often cloud operators, site reliability engineers and IT administrators, a relatively small scope of identities that pack a massive punch.
By taking the Blueprint’s risk-based approach to prioritization, Novice organizations can measurably drive down risk while making the most of existing capabilities, controls and integrations. The same logic applies to organizations at every maturity level. As you expand your toolset and mature your capabilities, a risk-based approach keeps you focused on the right identities and personas at each stage of the journey.
Building Your Identity Security Plan
To get started, develop a strategy for maximizing the impact and value of current controls – this is especially important for organizations in the early stages of maturity.
This should culminate in a program roadmap that sets the direction for the Identity Security initiative and leads to advanced levels of maturity. Therefore, aligning Maturity Level 1: Novice with Stage 1 of the CyberArk Blueprint becomes an important fundamental strategy when building a plan that seeks to maximize risk reduction and impact.
However, it’s important to remember these are two distinct models, and explicit one-to-one mapping of maturity levels and Blueprint stages shouldn’t be the goal. Additionally, every organization is unique. To take full advantage of this foundational guidance, you must understand your organization’s current risk state and capabilities. You’ll also need to take stock of internal priorities. For instance, are you facing new audit and compliance requirements, advancing a Zero Trust initiative or reacting to an internal security incident or breach? While these are all valid reasons for prioritizing security efforts, they alone should not define your plan. Initiatives driven by internal priorities must also consider the level of risk, impact of mitigation and level of effort, as well as relevant industry guidance to help drive informed decision-making.
Finally, your organization’s desired business outcomes (the goals, objectives and specific results you seek to achieve through the Identity Security program) must also be factored into roadmap design. You can learn more about incorporating multiple organization-specific factors into a roadmap in our Success blog post, “Create Your Identity Security Roadmap with the CyberArk Blueprint.”
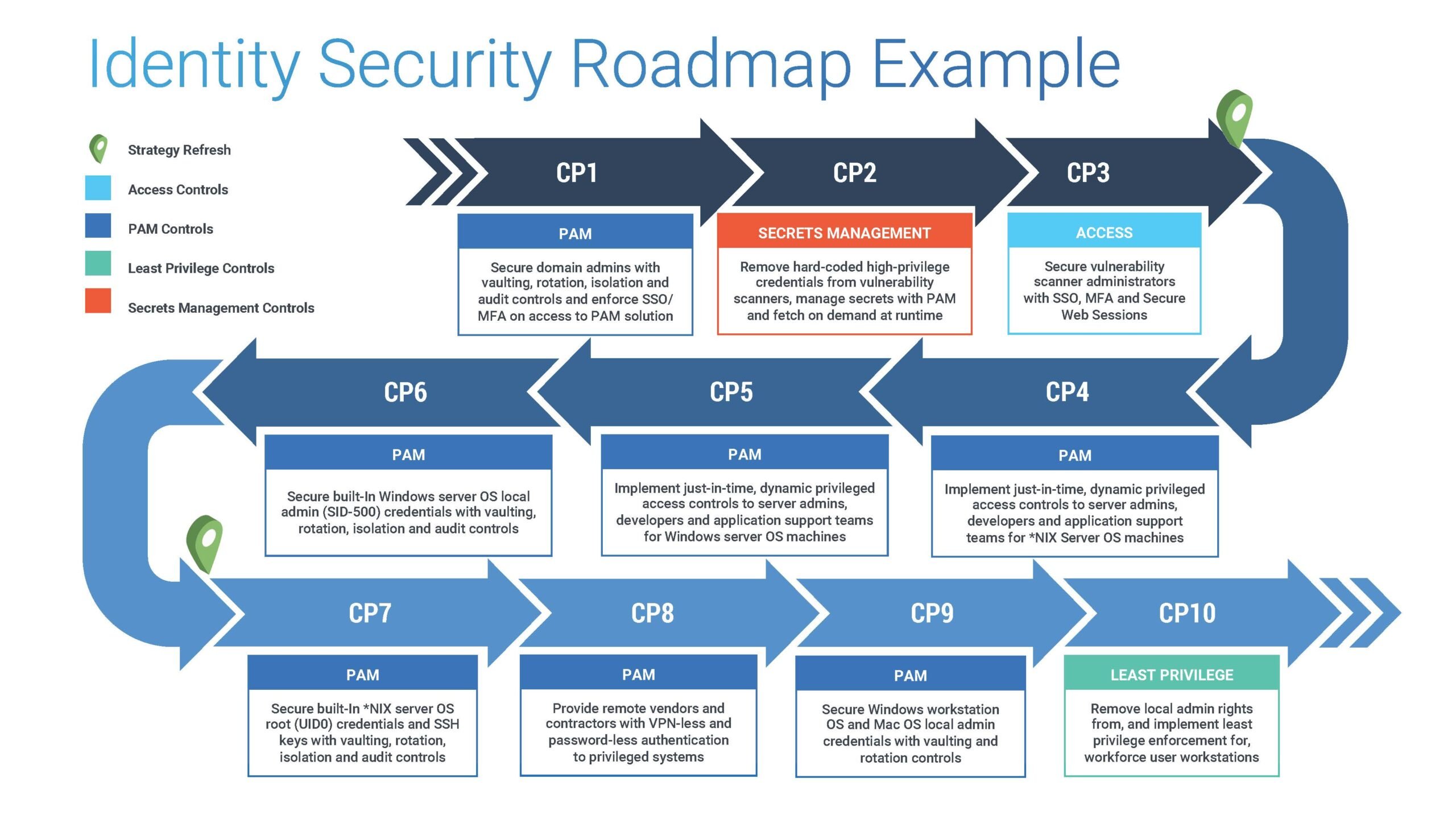
Figure 2: Identity Security Roadmap Example
By marrying all these together, you can create a winning Identity Security roadmap that’s tailored to your organizational needs and risks, but still reflective of industry and security best practices.
As mentioned, since every organization is unique, there is no one-size-fits-all way to approach Identity Security. However, we hope this information provides some useful prioritization guidance and clarity as you mature your strategy. You can also explore ways to use the CyberArk Blueprint to help achieve specific goals, from understanding the identity attack surface and assessing your security posture to learning best practices and building your roadmap.
Source: ESG White Paper, The Holistic Identity Security Maturity Model, February 2023.