Cloud Identity Security Success: 3 Critical Factors
Today, more than ever, security is all about identity. Especially in the cloud, the central management and proliferation of cloud services means that with the proper identity and permissions, one can do almost anything (legitimate or malicious).
Product management has been my focus for over 15 years, and in that time, I have experienced multiple IT and ecosystem transformations. Let me tell you, it’s never easy for organizations. When I joined CyberArk three years ago, I wanted to understand how our customers dealt with cloud transformations. Specifically, I wanted to know how identity security programs could transform with IT. I talked to many experts within the organization and with customers, trying to understand what’s most important in implementing a cloud identity security program – and to deduce from these insights where our development focus should be.
Given my experience, the following are what I consider to be the key factors to cloud identity security success:
1. Smart Risk Reduction
Some would say that security is all about systematic risk reduction. Many solutions today utilize cloud APIs and central management and specialize in providing cloud security posture. These solutions aim to identify risks to your cloud configurations and help prioritize them; identity and access management (IAM) is an essential part of that.
But we don’t just want to get recommendations to fix misconfigurations. We need meaningful insights and to take action quickly. For example, we want to swiftly identify low-hanging fruits like those dormant identities just sitting there and increasing your attack surface. We also want to determine high-risk identities such as shadow admins – identities and roles that can elevate their own permissions and move laterally so we can rapidly take action to secure them.
As we systematically reduce risk, we want to keep to least privilege principles and remove standing access in favor of zero standing permissions. We should have a solution built to drive immediate actions from insights.
2. User Experiences that Encourage Adoption
As enterprises implement new security tools, they face a familiar trade-off: traditional security controls can impact users, in ways that slow down their ability to do their jobs.
Imposing security upon IT teams is one challenge, but enforcing controls on developers or DevOps is almost impossible. The cloud was built for speed, and no dev team would ever agree to be slowed down. And for that fact alone, I know that the successful adoption of security solutions is all about end user experience.
When we secure access to sensitive resources and services, we should always allow end users to use their native tools, giving them an experience with the least friction. Sometimes, we can improve their lives with small productivity enhancements, like giving them a personalized view of available systems and roles they can connect to.
Let’s look at another example of a developer adoption challenge: for security teams to ensure secrets management practices are used to secure application credentials (non-human identities). This is why I’m proud of our capabilities that allow developers to keep using their preferred cloud-native solutions without making any changes to their application – while CyberArk secures and governs those secrets on the backend. It’s an excellent way to help ensure both developers and security teams achieve their goals.
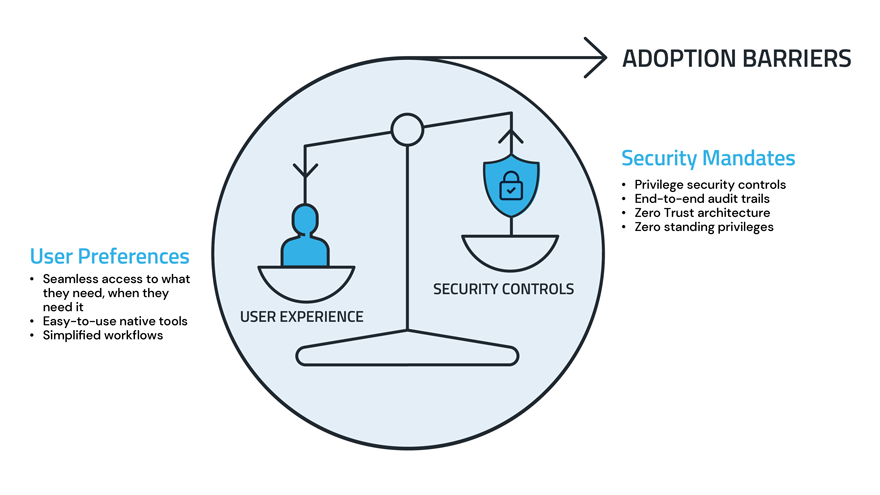
A simplified view of a common security/usability trade-off
3. Fewer Security Tools
Now that we all agree on the importance of the end user experience for successful adoption, we should also keep in mind that admins and security teams have to use the security tools themselves. With security being top of mind, the explosion of solutions and tools is enough to give anyone a headache. Consider a cloud security architect or IAM expert who needs to fully understand and operate the myriad solutions for securing their environment. They need to manage native cloud provider tools and services (and multiply that threefold for a multi-cloud strategy) and related solutions for IGA, IDP, PAM, CIEM and secrets management. These systems must work harmoniously, feeding one another and integrating with other key systems such as ITSM and SIEM solutions. It is no wonder that a recent ESG report showed that 54% of organizations prefer a platform approach with unified controls from fewer vendors.
So maybe it’s all about running an efficient operation – using fewer tools to manage your IAM needs. This can help ensure those security solutions can be more easily installed and efficiently managed to succeed.
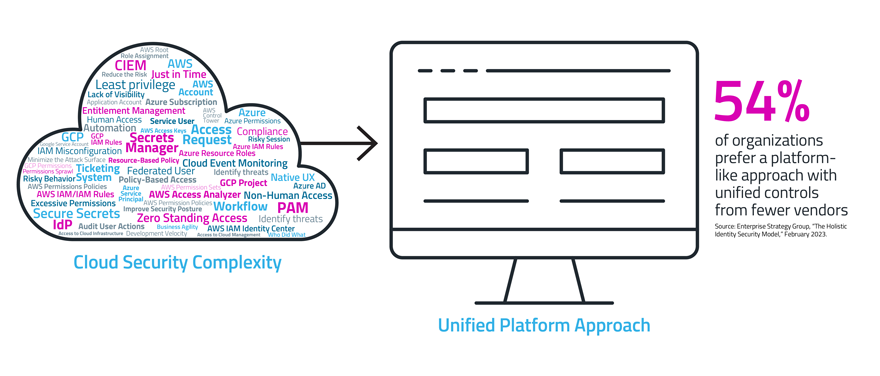
Better Together: People, Processes and Technology
Considering that no one key to a successful cloud identity security program exists, we should look beyond just pure technology, features and capabilities. Instead, we should consider the real-life challenges of implementing a large-scale, multi-cloud and multi-system environment. We should think of processes within organizations to keep developers (end users) happy. And we should provide admins with platform-based solutions to manage an efficient operation, identify IAM risks and mitigate them with an integrated solution.
Yonatan Klein is director of product management, Cloud Security at CyberArk.