Bad Droid! How Shoddy Machine Security Can Topple Empires

The need for strong identity security protocols for humans has been a given for years. Your organization likely has multiple layers of controls to ensure that access to sensitive assets is limited to those that need it. But a certain large, global (well…multi-global) organization that comes to mind on this May the Fourth also had layers of human identity controls that adhered to the principles of least privilege.
And yet a small, scrappy group of attackers exploited their security protocols, exfiltrated their most sensitive data and destroyed the empire – er, organization – from within its own network. How did this happen?
Machine identity security is just as crucial, if not more so, to organizations defending against the rise of identity-based cyberattacks. After all, machine identities now outweigh human ones in your average organization by a factor of 45x, according to CyberArk research. So how do you make sure those are secure too? Let’s take a look at what happened to this fictitious organization – we’ll call them Empire Inc.
Human Identity Security Is All Well and Good…
Like many organizations, Empire Inc. had multiple layers of human identity security controls, some of which were built into their…employees’ uniforms.
The first were something that Empire Inc. called “code cylinders,” but you could think of them similar to privileged account credentials. Some employees, those who required lower privileged access, only had one, while those higher up in the organization could have access to several. These credentials uniquely identified each user with their personal security code and clearance level, providing authentication. Each sector of the organization also required a different code cylinder, ensuring there was a separation of duties that prevented potential conflicts of interest or fraud by reducing the damage any one individual could do beyond their job scope. Finally, these credentials provided session monitoring and a detailed audit trail of each user’s activity, including real-time reporting of suspicious behavior and unnecessary access to sensitive files and resources.
Rank insignia plaques also signified each employee’s role, enabling Empire Inc. to provide granular access control and authorization based on the user’s role, known as role-based access controls (RBAC).
All of these security measures did a great job of enforcing the principle of least privilege when it came to the human employees of Empire Inc.
But You Can’t Forget Your Non-human Identities
Empire Inc. made one big mistake, however. While they had an iron-fisted grip on human identity and access control, they completely forgot about the machines that also had access to their environments and systems. And even when they did acknowledge their machine identities, they wrongly assumed that the droids couldn’t cause any real harm to such a large organization.
Early on in the attack — which spanned several months as the threat actors diligently worked their way through Empire Inc.’s layers of security — one machine gained highly privileged access and was allowed to exfiltrate sensitive data that it had stolen to pass it along to its human allies. The security controls spotted the exfiltration but shockingly let the machine — we’ll call him “ArrToo” — go as they didn’t detect any “lifeforms” involved. By not applying the same strict controls it had for human employees when it came to granting access and auditing user activity, Empire Inc. left a giant hole in its security defense.
From there, the attackers continued to exploit Empire Inc.’s ignorance of the power machine identities could wield. Because of Empire Inc.’s lack of proper authentication protocols for machine identities (which they had for humans), ArrToo was able to gain access to every environment within the organization, as well as all of the resources within it, without an authorization check catching him. Locks were meaningless to ArrToo, who bypassed them with ease and exfiltrated additional data from Empire Inc. Eventually, ArrToo’s activities, unmonitored by the security team at Empire Inc., allowed its human allies to launch a successful attack against Empire Inc. and bring down their entire network.
Zero Trust: Adopt an “Assume Breach” Mindset
Let’s try and give Empire Inc. the benefit of the doubt. Perhaps they knew a rogue machine like ArrToo would be able to bypass much of their security controls, hence why they refused to allow machines access to many places in their organization. Their focus was mainly on keeping threat actors from breaching their perimeter. The problem with this approach, however, is that it allowed the attackers to turn a small breach into a much larger disaster.
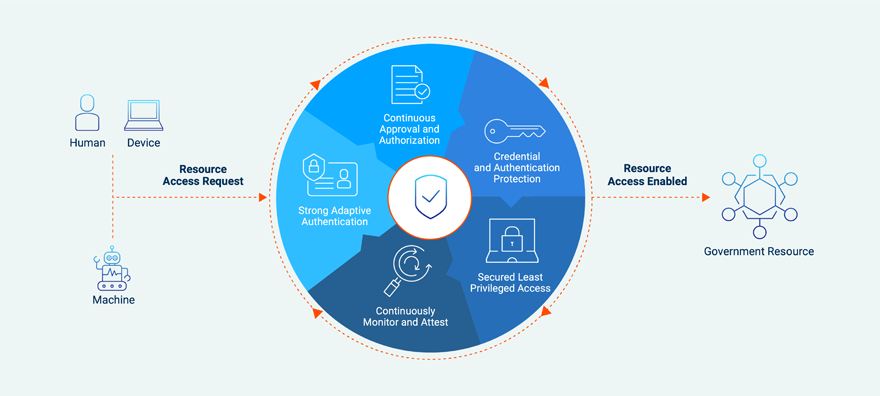
Instead, faced with constant cybersecurity threats, enterprises need to focus on what they can control to mitigate their risk and potential exposure. Because there is no longer a well-defined IT perimeter, the threat landscape is now asymmetric, making a Zero Trust security mindset essential. Protecting non-human identities and the secrets that they have access to — which can grant them high levels of privileged access to multiple sensitive resources — is critical to defending against the next attack. Organizations need to assume that they’ve already been breached and build layers of security to ensure both human and non-human identities have the right amount of access.
Security teams need to holistically manage access across the entire enterprise without silos or blind spots, with the ability to automatically rotate credentials as needed. A centralized secrets management system is the best option for authenticating, authorizing and auditing non-human access because it allows organizations to fully understand who has access to what and to automatically rotate or revoke access as needed.
To learn more about how secrets management can help secure non-human identities (and for some more fun discussion on Empire Inc. and the scrappy attackers that brought them down), join me for our webinar, “Are These The Droids You’re Looking For – Bringing Balance to Application Identities.”
And May the Fourth be with you!
John Walsh is a senior product marketing manager at CyberArk.