How Secure is Automotive Digital Identity?

In the automotive industry’s fast lane, the fusion of digital innovation with vehicular engineering has revolutionized how we manufacture, drive and protect our vehicles. It also helps to ensure our cars are safeguarded against cyber risks. And it’s at this juncture that identity security emerges as a critical priority – serving as both a shield and a guide, leading the industry through the complexities of cybersecurity in automotive challenges with unmatched precision.
Defending the Digital Road
Imagine the automotive industry as a vast, interconnected network of highways, where every vehicle – from family sedan to motorcycle to the most sophisticated autonomous car – communicates within a world far beyond the asphalt through connected vehicle technology. This seamless interaction is powered by vehicle-to-everything (V2X) technology, enabling connected cars to communicate with one another – and with infrastructure, pedestrians, networks and even the power grid. Connected vehicle technology forms the backbone of modern automotive safety and efficiency, facilitating real time sharing of crucial data such as traffic conditions, weather updates and road safety alerts.
However, it also introduces novel challenges in cybersecurity, making the role of secure identity verification more critical than ever at the manufacturing stage. Each connected car, acting as a pivotal node in the safety and operational efficiency of our digital highways, relies on a next-generation automotive and mobility security solution to safeguard the integrity of data exchange and protect against cyber threats to help ensure the seamless functionality of this intricate and interconnected network.
Elevating Automotive Security Through Identity Protection
The mastery of securing the privileged pathways of the automotive manufacturing ecosystem acts like an invisible shield. From the initial design sketches to the factories that bring new cars to life, a comprehensive approach to identity security helps ensure that every entity, human or machine, is thoroughly verified, authenticated and monitored.
The journey from innovation to vulnerability can unfold through a sophisticated attack chain in the rapidly evolving automotive industry. Sometimes, it might begin with credential theft, where attackers mine sensitive information through methods like social engineering. These malicious actors, whether external or internal, navigate an organization’s digital ecosystem, moving laterally across systems or vertically to higher privileges, aiming to disrupt operations or steal valuable data. Understanding and dismantling this attack chain, with a strategic approach for identity security, is critical for automotive leaders to shield their operations and vehicles against today’s multifaceted cyber threats.
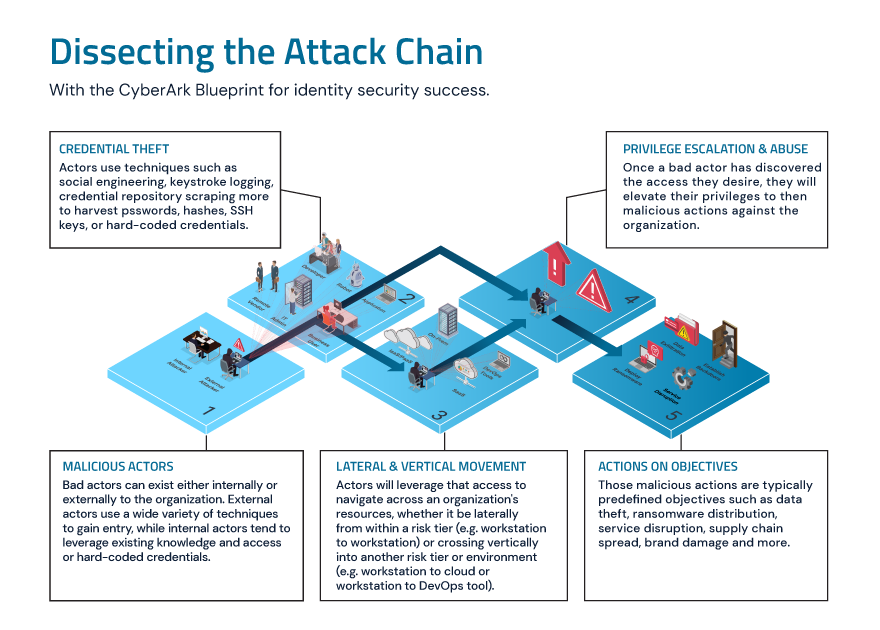
For manufacturers, this means securely guarding their blueprints, production secrets and assembly output.
Navigating the Top Seven Automotive Cybersecurity Challenges with Identity Security
Understanding the seven critical areas of automotive cybersecurity is crucial, as identity security can significantly enhance your organization’s preparedness and strengthen its stance against potential breaches. This strategic knowledge enables you to stay ahead in safeguarding against identity-related vulnerabilities within the automotive sector:
- V2X communication. Today’s vehicles are manufactured with the capability to communicate with one another, and their infrastructure and identity security act as trusted couriers that validate human and non-human identities in the automotive manufacturing process.
- Identity verification. Cyber threats loom like bandits in the digital expanse. Advanced identity verification acts as a vigilant patrol, safeguarding the credentials and secrets of administrators, users, applications, and machines interacting with connected vehicles and data.
- Regulation and compliance. The automotive world’s regulatory environment is a labyrinth and ever-changing. A robust identity security strategy is like GPS, guiding manufacturers through compliance and helping to ensure a smooth regulatory journey, which is a growing challenge for automotive manufacturers as cars become increasingly data-centric.
- Supply chain. Picture the automotive supply chain as a network of roads and bridges. A unified identity security approach provides rigorous checkpoints, verifying each component’s integrity before it enters the production line, underpinning the seamless integration of connected devices.
- Data privacy. Strict identity security protocols secure this data within cloud and enterprise environments against unauthorized access, safeguarding the manufacturing of connected vehicles.
- Market growth. As the realm of automotive cybersecurity widens like an expanding network of roads and infrastructure, scalable identity security solutions help provide safe passage across a burgeoning ecosystem of connected devices.
- Collaboration. Automakers and cybersecurity entities must unite to share insights and strategies. Secure identity management facilitates this collaboration, helping to ensure the secure exchange of information and bolstering the collective defense of connected vehicles throughout the auto manufacturing process.
Driving Toward a Secure Horizon
Cybersecurity leaders can help steer their organizations toward secure, modernized processes with a comprehensive identity security strategy. Learn how a leading manufacturer reduced operation time by 87% while improving security.
Brian Carpenter is a senior director of business development, and Christian Goetz is a director of presales success at CyberArk.
Editor’s note: The complexities of the automotive industry require a holistic platform-based approach to secure cars of the present and future. Take a spin into this topic and listen to our Trust Issues podcast episode, “What’s Driving the Future of Automotive Security,” with guest Kaivan Karimi, Global Partner Strategy and OT Cybersecurity Lead – Automotive Mobility and Transportation at Microsoft. Karimi discusses the emphasis on identity security, data sovereignty, data privacy and compliance as we collectively navigate technological advancements in the automotive industry.