Post-quantum cryptography (PQC): how to build resilience while padlocks still work

This blog is the second part of a two-part series on post-quantum cryptography (PQC). In Part 1, we explored how the Harvest Now, Decrypt Later (HNDL) strategy has moved from crypto-conspiracy theory to a real threat model. This follow-up dives into how forward-thinking enterprises are already operationalizing PQC in their day-to-day security efforts—and how your team can take practical steps to do the same before quantum risk becomes quantum reality.
If you’re like most organizations, you’re waiting for quantum computers to at least come within radar range before you mount your defenses. This seems reasonable. After all, the cryptocalypse has become the slowest-moving inevitability in tech. The problem is that threat actors aren’t waiting. They’re collecting encrypted data now, betting on a future where the codes are crackable as fortune cookies.
Organizations must turn apathy into action to protect data, infrastructure, and future operations. CyberArk suggests a practical three-phase attack plan: map your risks, model the migration, and mobilize your post-quantum cryptography (PQC) strategy. Yes, we know “mobilize” is doing a lot of work in that sentence. It implies executing, testing, scaling, and everything in between. However, taken in steps, each phase helps build toward crypto agility—the ability to pivot cryptographic algorithms without downtime (or existential crises).

Step 1. Map your cryptographic risks for PQC readiness
Before you can secure your cryptographic systems, you need to know where they are, how they’re used, and what risks are tied to them. Start by taking these steps:
- Inventory your cryptographic assets. Catalog and map all certificates, keys, secrets, and tokens across human and machine identities, workloads, cloud platforms, and DevOps pipelines.
- Evaluate your authentication material. TLS certificates, SSH keys, code-signing certificates, vaults—anything holding a secret deserves a wellness check. Understand how access tokens are generated and identify which identities—human or machine—control sensitive operations.
- Centralize visibility. Use certificate lifecycle management (CLM) to eliminate shadow certificates and prepare for rotation at scale.
Step 2. Plan a smooth PQC migration: make a quantum leap, not a faceplant
You can’t forklift quantum-safe encryption overnight. And trying to do so could result in outages, chaos, and rage-quitting. That’s why it’s critical to design a plan that won’t collapse under its own complexity or tank your uptime.
Focus on three planning pillars:
1. Design for agility
Think modular, not monolithic:
- Architect systems to support seamless cryptographic algorithm swaps—without requiring a full rip-and-replace.
- Ensure cryptographic services (e.g., PKI, certificate management) are modular and interoperable—think plug-and-play, not duct tape.
- Favor tooling that allows dual algorithm support (classical and PQC) during transitional periods.
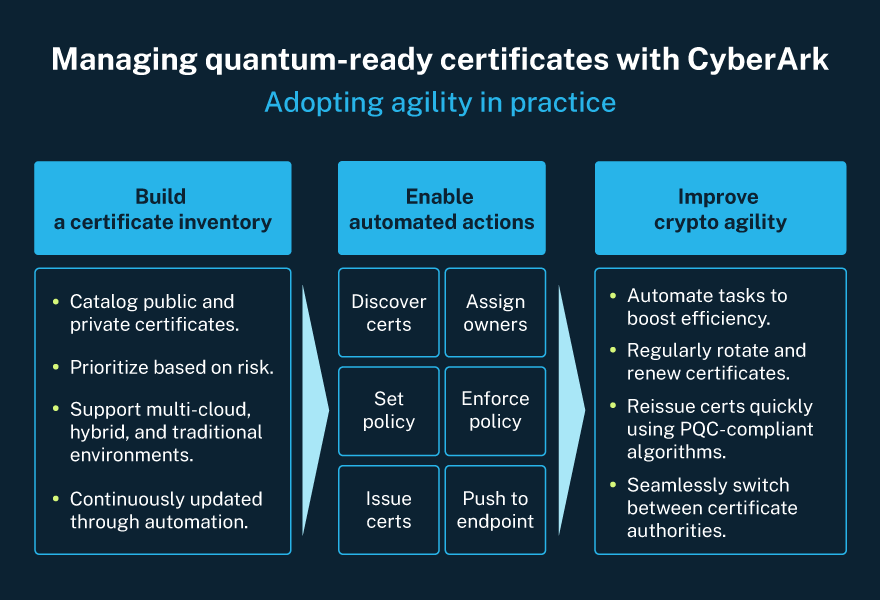
Figure 1. How to build a certificate lifecycle strategy from inventory and automation to crypto agility.
2. Time it right
Don’t derail your roadmap:
- Plan cryptographic upgrades to coincide with natural inflection points like certificate expirations, cloud migrations, Zero Trust or identity modernization efforts.
- Establish fallback mechanisms, such as test environments, dual encryption, or staged rollouts. Murphy’s Law is undefeated.
3. Check your ecosystem
Can your infrastructure handle PQC?
- Are your crypto libraries, CAs, and identity providers onboard—or stuck in 2011?
- Audit CLM vendors and DevOps pipelines for PQC support and automation capabilities.
- Start auditing vendors now. Confirm support for PQC adoption—especially for certificate authorities, cryptographic libraries, and identity platforms.
- Identify components that need replacing, reconfiguring, or retiring with a quiet but dignified burial.
Step 3. Operationalize your PQC strategy across the enterprise
This is where theory meets reality—and reality fights back. Focus on reducing high-risk dependencies and making PQC adoption sustainable.
1. Strengthen identity controls
- Move toward passwordless access and adopt PQ-safe certs where available.
- Reduce standing access, enforce least privilege, and automate credential management. If your team is still manually rotating secrets, it’s 2025—time to move from surviving to thriving. Thank you for coming to my TED Talk.
2. Secure machine identities
- Lock down workloads across on-prem, cloud, hybrid—the whole circus.
- Use modern CLM integrated with Kubernetes and container platforms to automate machine identity provisioning, renewal, and revocation.
- Automate credential lifecycle management and start provisioning quantum-safe keys now, not after a breach postmortem.
3. Retire static secrets
- Static credentials are sitting ducks for Harvest Now, Decrypt Later attacks.
- Shift to ephemeral access models like just-in-time (JIT) credentials. And seriously, get rid of those hardcoded secrets. They’re not legacy—they’re liabilities.
To limit how long secrets are exposed, organizations need to shift to ephemeral access models like JIT credentials. It’s equally critical to regularly rotate or phase out hardcoded and unmanaged credentials—because anything stolen today could be wide open in a post-quantum world.
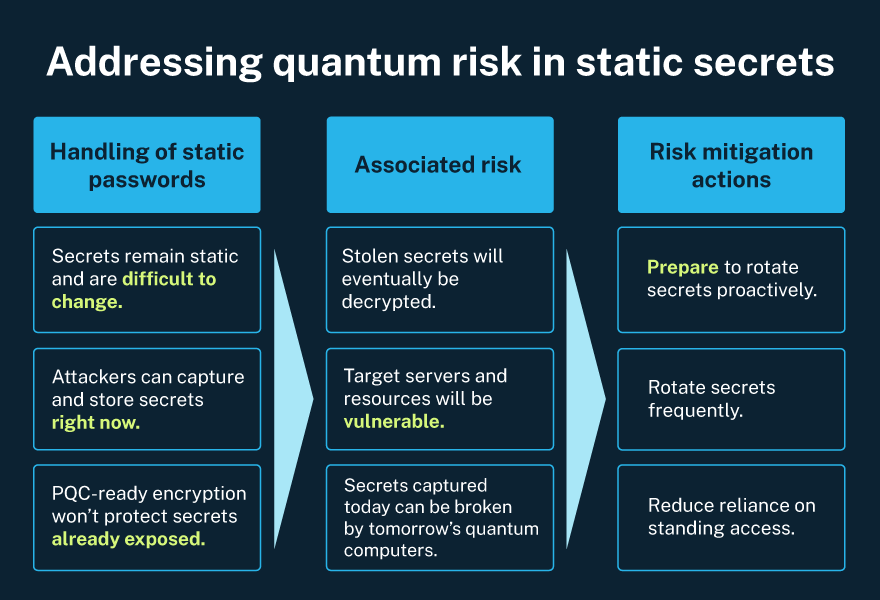
Figure 2. How static passwords create risk—and what to do about it.
Making the business case for post-quantum cryptography
PQC prep isn’t just for paranoid cryptographers and risk managers. The same groundwork supports:
- Certificate automation
- Machine identity hygiene
- Zero Trust access control
Translate the benefits into boardroom language to make the business case. Emphasize that quantum readiness will help minimize future regulatory exposure, protect ongoing digital transformation investments, and reduce long-term identity-related risk across the organization.
Getting executive buy-in isn’t just a messaging task—it’s a strategic must. Highlight how PQC readiness also enhances operational resilience, audit performance, and Zero Trust maturity. Make it clear that this is a shared mission between security, DevOps, and IT.
These aren’t just technical wins—they’re strategic moves safeguarding the business as the threat and compliance landscapes evolve.
Executive priorities for the post-quantum era
Today, CISOs need to think in longer arcs—not because the quantum threat is imminent, but because the response timeline is. Certificates, authentication protocols, machine identities, and encrypted credentials form the connective tissue of security architecture. And they are precisely what quantum systems threaten to undermine.
Enterprise security platforms are beginning to embed quantum-safe principles—CyberArk among them—to help organizations adapt before disruption hits. As an executive, you ensure the business isn’t caught unprepared. That means:
- Demanding visibility into where cryptography underpins critical operations.
- Prioritizing systems based on risk and regulatory exposure,
- Aligning PQC efforts with transformation initiatives (Zero Trust, cloud, identity modernization), and
- Choosing partners that enable cryptographic agility without rewriting your entire stack.
In the post-quantum era, delay isn’t just a risk—it’s a strategic liability. Every security team must track these operational priorities, starting yesterday. Organizations that start preparing now will be better equipped to adapt, comply, and lead as quantum disruption approaches. For a deeper dive into how identity security and quantum readiness intersect, check out our new book, “The Identity Security Imperative: A Leader’s Guide to Securing Every Identity.”
Missed how this all started? Check out Part 1, to see why post-quantum prep can’t wait—even if your padlocks still work.
Nick Curcuru is a product marketing director at CyberArk.