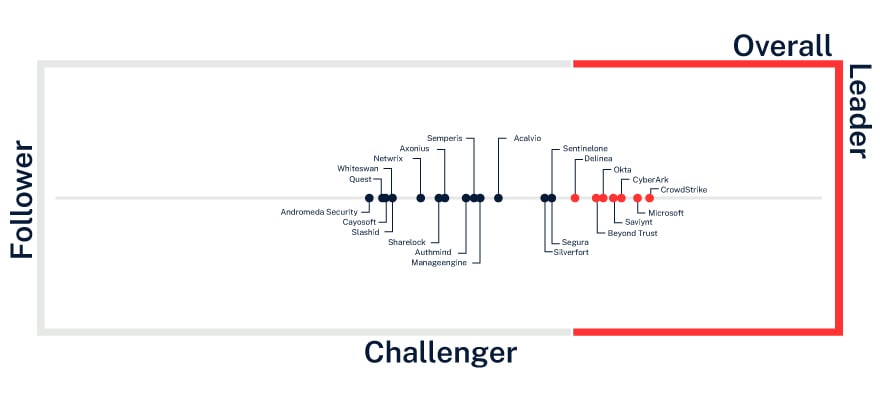
CyberArk named overall leader in 2025 KuppingerCole ITDR Leadership Compass

KuppingerCole has recognized CyberArk identity threat detection and response (ITDR) as a leader across all categories: overall, product, innovation, and market in its 2025 KuppingerCole Leadership Compass for Identity Threat Detection & Response.
Why ITDR matters
As cloud adoption, automation, and third-party access expand, identities have become the primary attack surface. Traditional controls such as single sign-on (SSO) and multi-factor authentication (MFA) play an important role, but they don’t address what happens after authentication. CyberArk TDR fills the visibility gap by continuously monitoring identity behavior across pre-login signals, authentication patterns, active sessions, and privilege use. It helps security teams detect misuse that authentication controls can often miss, and ties detections to automated response actions. Analysts now treat ITDR as a core element of identity security because it operationalizes detection, response, and continuous posture management across the entire identity control plane.
What KuppingerCole highlighted about CyberArk
In its assessment, KuppingerCole analysis called out CyberArk capabilities that map directly to operational outcomes for security teams:
- ITDR embedded inside an identity platform: Because ITDR and posture management are delivered natively inside the CyberArk Identity Security Platform (not bolted on), detections come with policy and privilege context which means teams can act immediately and safely. This leads to fewer false positives, faster containment, and remediation.
- AI-driven detection and remediation: Our behavioral analytics and AI help convert high-fidelity detections into automated, risk-based actions (rotate credentials, isolate sessions, step-up auth). This results in less manual triage, faster recovery, and lower business exposure from identity attacks.
- Protection for the riskiest identities and sessions: By combining threat-based access controls with privileged session isolation and adaptive policies, CyberArk reduces the chance that a high-value account becomes a breach vector. That protects the accounts that matter most and limits how far an attacker can move if they do get in.
- Early discovery of hidden identity risks: CyberArk discovers shadow/service accounts and risky credentials that often go unnoticed. With CyberArk, organizations can gain immediate visibility into forgotten or over-privileged identities so they can remove or secure them before they’re abused.
- Built to work inside your SOC and security stack: Deep integrations with SIEM, SOAR, ITSM, and XDR let identity signals feed analyst workflows and automated playbooks, and let SOC detections enrich identity investigations. That means faster, coordinated responses across teams, not alerts that sit in isolation.
The CyberArk advantage: A unified approach to identity threat detection and response
What ultimately differentiates CyberArk’s approach to ITDR is that it isn’t delivered as a standalone detection tool. Instead, ITDR is built into a unified identity security platform that already governs access, privilege, and identity risk.
That unified foundation gives richer context, higher-confidence detections, and the ability to take precise, automated action in real time. For security teams, that means faster containment, reduced manual effort, and greater confidence that response actions won’t disrupt legitimate access.
As identities multiply across humans, machines, and AI, security can’t rely on disconnected signals: “ITDR isn’t about more alerts, it’s about shrinking the identity attack surface and containing attacks faster to minimize impact”, said Yonatan Klein, director of product management at CyberArk.
The future of ITDR and identity security
ITDR is maturing from a standalone capability into a central pillar of identity security, increasingly converging with discovery and posture management to reduce identity exposure before and during attacks.
Modern protection now requires more than detection alone. Organizations need continuous discovery, entitlement posture assessment, and automated containment so teams can find shadow accounts, fix risky credentials, and shrink their attack surface— before adversaries exploit it.
CyberArk’s leader placement in the 2025 KuppingerCole ITDR Leadership Compass reflects that strategy. We believe identity security works best as a unified platform that sees the full identity infrastructure, continuously hardens posture through discovery and remediation, and then rapidly contains attacks with native, policy-aware actions.
Additional Resources:
- Download the CyberArk Threat Detection and Response Solution Brief
- Read the full 2025 KuppingerCole Leadership Compass for Identity Threat Detection & Response (ITDR).
Yev Koup is the senior product marketing manager for access management at CyberArk.