DORA Compliance: A Security Wake-Up Call

The Clock is Ticking
The Digital Operational Resilience Act (DORA) is about to shake things up in the EU, and if you’re not ready, it’s time to get moving.
With the new regulations set to take effect in January 2025, organizations are facing a critical deadline. DORA differs from other regulations like GDPR or NIS2 – which also lay out security requirements for businesses – because it specifically focuses on the financial industry. This means insurance companies, investment firms, credit institutions, banks and some of their third-party providers, like data centers or software providers, are obligated to comply. And while there are some overlaps with other security frameworks, DORA has a particular mission to strengthen the resilience of the European financial system.
But here’s the thing: DORA isn’t just another box to check on your compliance list. It’s a wake-up call – a nudge for organizations to embrace security foundational practices they should have already embedded into their operations.
How Security Best Practices Naturally Ensure Compliance
Let’s be real – CIOs, CISOs and security teams are well aware of the risks that are out there. You’re not complacent or cutting corners; you’re doing everything you can within the constraints of time, budget and resources. The challenge? Juggling priorities while keeping the bottom line in mind.
To truly satisfy DORA and other requirements, companies must take a holistic identity security approach. By protecting all identities with access to any sensitive resource, companies can enforce least privilege, streamline audits and provide detailed reporting.
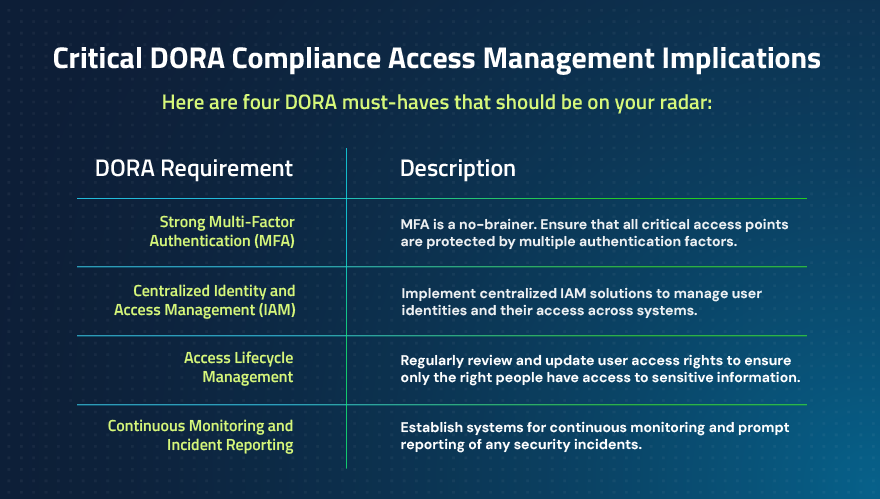
In addition, DORA is spotlighting access control measures – like single sign-on (SSO), multi-factor authentication (MFA) and identity lifecycle management – which are already considered security best practices across the industry. It can be tempting for companies to focus on innovations and threats like AI, which certainly merit attention. But we sometimes fail to cover the basics.
Instead of viewing DORA as just another regulatory headache, consider it an opportunity to strengthen your organization’s defenses. Regulatory pressure can catalyze internal change, helping IT security leaders secure the necessary buy-in from stakeholders and the board. In a world where cyber threats are constantly evolving, staying one step ahead isn’t just a necessity—it’s a competitive advantage.
Scrutinizing Traditional Access Controls
DORA places a significant emphasis on access control, and for good reason. In many security breaches, unauthorized access is the first domino to fall, leading to data breaches, ransomware attacks and other costly incidents. The 2024 Verizon Data Breach Investigations Report (DBIR) found that attacks through web applications specifically have increased 180% in the last year, and 77% of those involved stolen credentials. Identity is the linchpin here, and that’s why regulatory authorities seek to safeguard it through measures like DORA.
By mandating robust SSO, MFA and lifecycle management, DORA is forcing organizations to take a hard look at who has access to what, when and how.
Not all Identity and Access Management (IAM) tools are created equal, so embedding sophisticated threat detection and response into those “basics” will also significantly strengthen resilience. For example, can you track user behavior and detect anomalies within your MFA solution? Can you adjust the MFA policy based on those behavior anomalies?
Or, as another example, take your SSO program. Sure, reducing the use of passwords can help mitigate risks for your users when it comes to federated identities. But again, SSOs are not all the same because some apps still require a username and password. So managing those credentials in tandem with SSO is even better.
For IT security leaders, DORA is an opportunity to reassess and refine their access control strategies. It’s not about doing the bare minimum to avoid penalties – it’s about building a resilient security posture that can withstand today’s sophisticated threats. Strong access control is the backbone of operational resilience, and DORA’s requirements align closely with what industry leaders already recognize as essential.
Gaining a Strategic Edge with Early Adoption
What sets industry leaders apart is their ability to see beyond compliance and leverage regulatory requirements as strategic opportunities. By embracing DORA’s requirements early, organizations can ensure compliance and gain a strategic advantage. For instance, investing in advanced IAM solutions meets DORA’s mandates, streamlining operations, reducing administrative overhead and enhancing the overall user experience. Similarly, implementing robust MFA doesn’t just prevent unauthorized access; it also builds trust with customers, partners and regulators.
Organizations that proactively adopt these practices are better positioned to respond to future regulatory changes, mitigate risks and capitalize on new business opportunities. DORA isn’t just a regulation – it’s a blueprint for building a more resilient, agile and secure organization.

Moving Beyond Compliance to Achieve Resilience
DORA is more than just a set of rules – it’s a chance to build a more resilient and secure organization. By adopting the best practices that DORA enforces, you’re protecting your company from fines and the ever-evolving landscape of identity-based cyber threats.
With the DORA deadline approaching, now is the time to act. Implement the latest access control technology to ensure your organization is compliant and truly secure.
Start by asking yourself: What policies, procedures and controls do we have in place to limit physical and logical access to information and ICT assets? Remember that necessary protections apply to employees and all third parties accessing those assets.
To explore DORA requirements more thoroughly, CyberArk has put together a DORA Compliance Identity Security Guidebook that provides examples of intelligent privilege controls that can help you meet those standards.
Navigating The Road Ahead
As digital transformation accelerates, regulatory frameworks will continue to evolve, placing even greater demands on organizations to maintain robust security postures. The companies that succeed will view compliance not as a burden but as an opportunity to innovate and lead. By embracing DORA today, you’re not just preparing for tomorrow but building the foundation for a secure and resilient future.
Laura Balboni is a senior product marketing manager at CyberArk.