You’ve Got Privileged Access Management… But Can You Keep Secrets Secure?

Threat actors don’t often need to execute the latest zero-day exploit or fight through firewalls to launch their attacks. Instead, they simply walk through the front door with stolen user credentials and take over legitimate digital identities. But while cyber attacks can be inevitable, damage and disruption are not. Organizations that take a privilege-centric approach to securing identities — both human and machine — are better positioned to stop attackers from reaching valuable assets and data.
In the Beginning, There Were Human Identities. Then, Non-Human Identities Emerged in Full Force
As organizations accelerate major digital initiatives and employ automation across their enterprise, continuous integration and continuous delivery (CI/CD) and DevOps methodologies have become the key to moving fast and staying agile. And applications — from traditional software solutions hosted in corporate data centers to modern applications running in the cloud — are the backbone of modern business. Identity Security programs must evolve and extend across these areas, weaving Privileged Access Management into the fabric of enterprise strategy and application pipelines.
Applications, DevOps tools and development and delivery pipelines are full of identities. It’s just that “identities” take on a different, non-human form in these dynamic environments: they’re applications, scripts, automation tools and myriad other machines. Each one requires secrets — SSH keys, API keys and other credentials — to access IT systems and other sensitive resources to do what they’re supposed to do. These secrets and credentials are highly attractive targets and the primary means for attackers to gain a foothold into an organization.
Application Secrets and Credentials are Everywhere
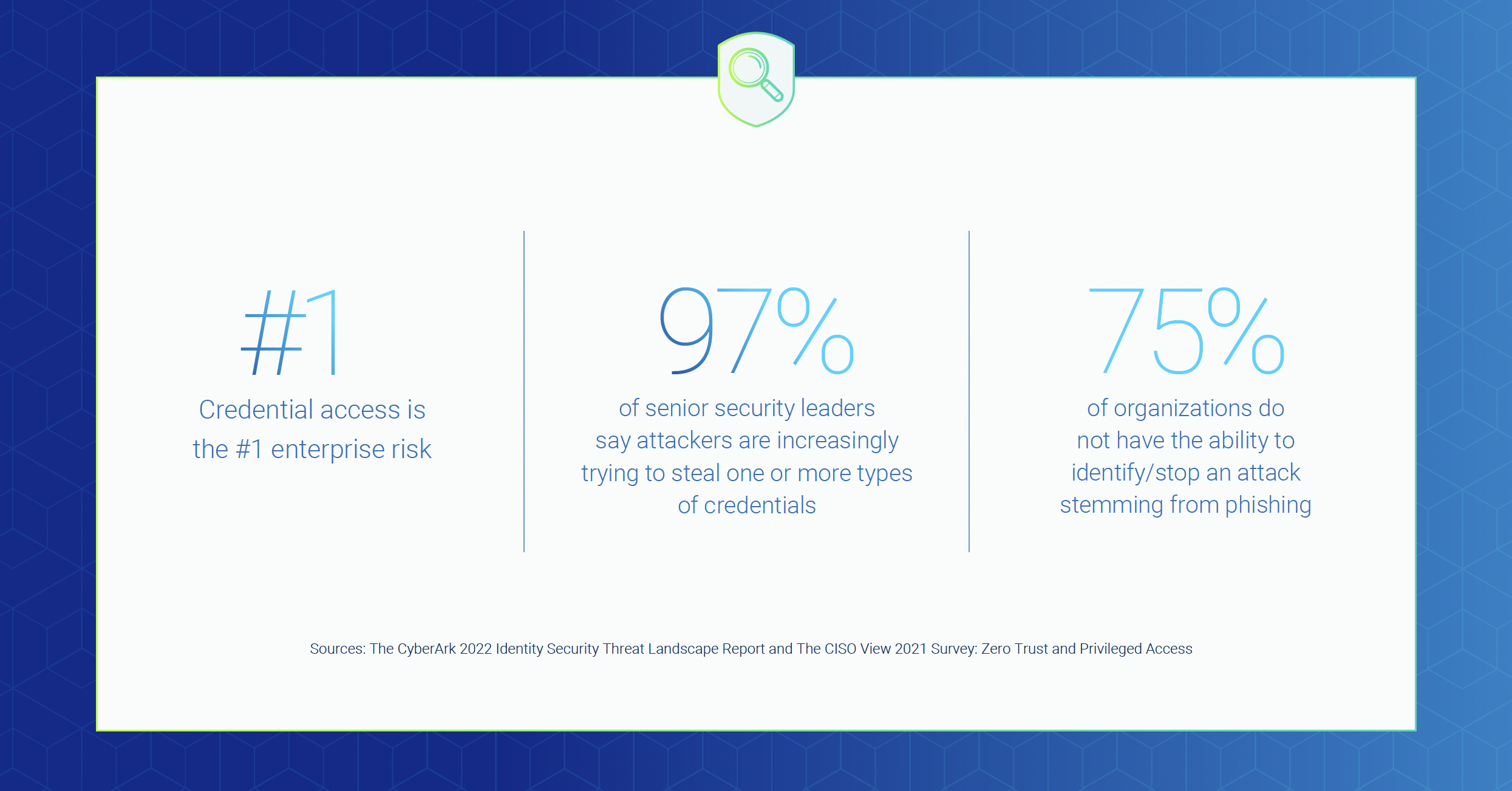
As non-human identities outnumber human identities by 45x on average, protecting this significant piece of the digital identity equation is imperative. Yet the CyberArk 2022 Identity Security Threat Landscape Report found that in many organizations, secrets management practices have not kept pace with the speed of digital innovation:
- Secrets are stored in multiple places, according to 87% of respondents
- Half said application credential security was left up to developers — a functional group known for emphasizing speed over security
- 80% agreed developers have more privileges than they need
The SolarWinds digital supply chain attack, CodeCov and other major incidents have made enterprise executives increasingly aware of the critical need to secure secrets in applications and development environments. Yet the CyberArk report revealed 62% of organizations have done nothing to secure their software supply chains post-SolarWinds even though 71% said their organization has suffered damages from a supply chain-related attack since the landmark breach.
Extending a Solid Privilege-based Security Foundation to Manage Secrets
According to Gartner®, security and risk management leaders responsible for IAM should “Expand the scope and benefit of your PAM programs by making full use of the full feature set of your PAM tools, especially secrets management for DevOps use cases, and CIEM for IaaS visibility.”1
With a solid Privileged Access Management foundation in place, security teams must now focus on expanding their Identity Security programs to encompass all facets of privileged access. That means securing human and non-human identities throughout the cycle of accessing critical assets — without slowing down development teams or delaying automation deployments.
It can be challenging to know where to start. Most organizations will need to secure an array of applications developed and maintained by different teams using different tools and hosted in different locations using various deployment models (on-prem, private cloud, public cloud or hybrid environments). Some applications are more critical to the business than others. Some are more mature and more difficult to adapt than others. And each application poses a special set of risks. Few security teams have the time or resources to take on all these challenges at once.
That’s where an agnostic, risk-aligned framework can help prioritize efforts by introducing Identity Security controls in stages, depending on your organization’s specific requirements. Take advantage of the following resources as you create a plan to give applications easy access to the secrets they need, while keeping credentials out of reach from attackers.
- Explore the CyberArk Blueprint for Protecting Application Secrets Everywhere
- Map your journey toward a mature, Identity Security program with privilege at the core with the Blueprint toolkit
- Visit the CyberArk Marketplace to explore powerful integrations, such as those with Red Hat Ansible that deliver simplified, automated secrets management throughout the DevOps pipeline
- Connect with CyberArk during the virtual Red Hat Summit May 10-11, 2022, to learn more about keeping secrets safe
1 – Gartner, Critical Capabilities for Privileged Access Management, Felix Gaehtgens, Abhyuday Data, Michael Kelley, Swati Rakheja, 19 July 2021
Gartner Disclaimers
GARTNER® is a registered trademark and service mark of Gartner, Inc. and/or its affiliates in the U.S. and internationally and is used herein with permission. All rights reserved.