Australia’s Growing Focus on Critical Infrastructure Cybersecurity in 2023

In recent years, several major cyberattacks targeted critical infrastructure in Australia, including a major telecommunication company, which suffered a devastating data breach in September 2022. Soon after this cyberattack, Australia’s biggest health insurer also faced a ransomware attack in October 2022 that caused systems to go down. Customers could not access services through the company’s website or app.
These cyberattacks severely disrupted these organizations’ operational rhythms and required extra resources to manage the fallout.
They also occurred on a global stage featuring rising geopolitical tensions and increased interconnectivity of individual countries’ critical infrastructures. Escalating threats and cyberattacks on critical infrastructure are now more than ever a collective, global issue.
In the wake of last year’s major breaches, the Australian government is pursuing a new cybersecurity agenda. While these were far from the first attacks on Australia’s critical infrastructure systems, they emphasized the growing threat. Governments worldwide sprang into action to strengthen critical infrastructure resilience and information sharing – with Australia notably taking several significant steps designed to fortify its own critical infrastructure.
Australia’s Steps to Strengthen Critical Infrastructure
In response to the major security breaches that unfolded in 2022, the Australian government has pushed for critical infrastructure reforms in 2023. As part of this effort, Australia’s Home Affairs Minister Clare O’Neil stated the government will set up a new national office for cybersecurity within Home Affairs and begin consulting on a new seven-year cybersecurity strategy.
One of the recent outputs of Australia’s concerted effort to fortify its critical infrastructure is its 2023 Critical Infrastructure Resilience Strategy (the Strategy), which defines critical infrastructure (CI) as, “… those physical facilities, supply chains, information technologies and communication networks, which impact the social or economic well-being of the nation or affect Australia’s ability to conduct national defense and ensure national security.” This definition expands the scope of previously established critical infrastructure sectors.

Australia’s critical infrastructure now consists of 11 defined sectors:
- Communications
- Financial services and markets
- Data storage or processing
- Defense industry
- Higher education and research
- Energy
- Food and grocery
- Healthcare and medical
- Space technology
- Transport
- Water and sewerage
The scope of what’s officially considered to be critical infrastructure varies from country to country. Examples of the most critical assets to protect, however, typically include data assets, such as healthcare medical records or defense department classified materials – along with physical assets, such as energy control systems and water treatment facilities. All critical sectors rely on computerized operating technology (OT) to function, which is converging with IT and exposing critical industrial control system (ICS) endpoints and other assets to aggressive threats like ransomware.
Australia’s Security of Critical Infrastructure Act 2018 (SOCI Act) creates a framework for the regulation and protection of critical infrastructure sectors. As part of Australia’s Cyber Security Strategy 2020, the Australian government updated the SOCI Act and introduced critical infrastructure law reforms with the aim to further protect and improve the resilience of the country’s critical infrastructure. More than 18 months after its original announcement, the full package of reforms to the SOCI Act has been implemented with important implications for critical infrastructure sectors in Australia.
Australia is one of many governments and industry regulators around the world that have recently enacted cybersecurity mandates and guidelines to protect critical infrastructure. Meanwhile, the updated SOCI Act became effective on Feb. 17, 2023. The act mandates that infrastructure entities must take steps to adopt the critical infrastructure risk management program (CIRMP), by Aug. 17, 2023. These entities must also comply with ISO 27001, or an equivalent of a NIST standard by Aug. 18, 2024.
Here is a closer look at the key cybersecurity implementations that the Australian critical infrastructure community will be making in 2023:
- Strengthening the government’s own cybersecurity infrastructure by updating and modernizing the systems and technologies used to protect sensitive data and networks, as well as increasing the number of trained cybersecurity professionals within the government.
- Implementing new regulations and standards for businesses to improve their cybersecurity posture to protect their data and reduce the risk of cyberattacks.
- Developing national cybersecurity to foster clear communication and cooperation between different agencies, which is vital in the fast-moving world of cybersecurity.
- Improving the cybersecurity of critical infrastructure by working with businesses and organizations that operate critical infrastructure systems, such as power grids and transportation systems, to ensure they are properly secured is a central focus of 2023.
- Cooperating internationally to address cybersecurity challenges in building strong partnerships with other countries in this area.
- Recognizing the need for a greater focus on cybersecurity literacy and training in 2023.
Australia’s Expanding Attack Surface
Australia’s efforts come at a critical moment. According to the Australian Cyber Security Centre (ACSC), many of the cyber incidents reported between July 2021 and June 2022 were associated with Australia’s critical infrastructure or essential services. In the 2021–22 financial year, 95 cyber incidents (approximately 8% of all cyber incidents the ACSC responded to) affected critical infrastructure. Since the implementation of amendments to the SOCI Act in April 2022, the ACSC has notified multiple critical infrastructure entities of cyber incidents and vulnerabilities on their networks.
At the same time, a confluence of technology trends continues to expand the threat landscape, opening new avenues for critical infrastructure attackers to steal information, disrupt systems and, increasingly, threaten human safety:
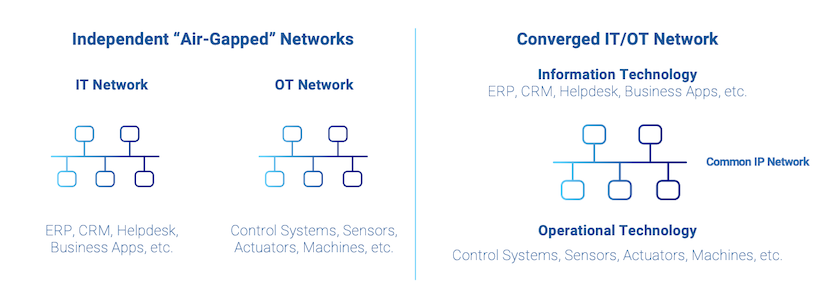
IT/OT network convergence. To reduce expenses, simplify operations and support industrial internet of things (IIoT) initiatives, many IT and OT networks are converging. However, this eliminates the “air gap” that once separated these two environments, providing a pathway for external threat actors to gain access to industrial control systems.
Push to standards-based OT. Industrial control systems were once based on proprietary hardware and special-purpose software. In the current shift toward standards-based OT, many systems run on Linux-based commodity servers and leverage commercial-off-the-shelf (COTS) software, making them vulnerable to software supply chain attacks.
Widespread cloud adoption. Critical infrastructure operators are adopting Software as a Service (SaaS), Infrastructure as a Service (IaaS) and Platform as a Service (PaaS) solutions to accelerate the pace of innovation, streamline operations and support IoT programs like Smart Grid, Smart City and Smart Transportation systems. While essential to digital transformation, these cloud services also provide new ways for adversaries to penetrate systems.
Critical Infrastructure Cybersecurity Regulations
Governments and industry regulators have already enacted cybersecurity mandates and guidelines to protect critical infrastructure against cyberattacks.
Identity Security is an essential requirement for most of these regulations. Identity Security helps critical infrastructure operators defend against cyberattacks, drives operational efficiencies, satisfies regulatory requirements and provides evidence of compliance. To fulfill these requirements, critical infrastructure operators might need to:
- Implement foundational controls to safeguard privileged access.
- Monitor privileged access activity and promptly notify authorities of a security breach.
- Demonstrate evidence of compliance to auditors on a regular basis.
Prioritizing Identity Security to Help Fortify Critical Infrastructure
Cybersecurity mandates and guidelines to protect critical infrastructure are becoming increasingly widespread. Many of these are grounded in a Zero Trust cybersecurity model, which assumes that all digital identities – human or machine – are implicitly untrusted and must be authenticated and authorized regardless of their network or location.
A Zero Trust approach protects modern operating environments by assuming all identities are implicitly untrusted and must be authenticated and authorized regardless of their network or location. Unlike a traditional perimeter-based security model, a Zero Trust architecture:
- Protects cloud-based IT and OT systems as well as on-premises IT and OT systems.
- Defends against inside threats as well as external threats.
- Provides inherent security for remote workers and mobile users.
Unlike a traditional perimeter-based security model, a Zero Trust architecture centers on identity – and requires a comprehensive Identity Security solution and strategy to encompass cloud-based IT and OT systems as well as those on-premises; to defend against internal and external threats; and to provide inherent security for remote workers and mobile users.
Identity Security offers a robust set of unified access controls to enable Zero Trust. Given the transformational characteristics of critical infrastructure, Identity Security is the modern security paradigm shift that helps to protect it efficiently and effectively.
In establishing an Identity Security approach, critical infrastructure operators can apply more stringent controls by tracking identities and enabling security controls to be seamlessly applied, based on risk in real time.
If you’re looking for tips on assessing your organization’s current strategy and tackling identity-related risk, check out the CyberArk Blueprint for Identity Security Success, a vendor-agnostic framework for defining a roadmap for Identity Security success.
Thomas Fikentscher is CyberArk’s Regional Director for Australia and New Zealand.