This message will self-decrypt in 5 years: why post-quantum prep starts now

This blog is the first part of a two-part series on post-quantum cryptography (PQC). In this piece, we explore why quantum threats are no longer theoretical. In Part 2, we’ll cover practical steps for building post-quantum readiness.
Security leaders have become digital-first responders. They perform triage on multiple emergencies every day, except with fewer thanks and more acronyms. When facing challenges like ransomware, AI-driven threats, misconfigurations, and compliance risks, apocalyptic intangibles like post-quantum cryptography (PQC) can feel like tomorrow’s problem. After all, quantum computing has seemingly been “a decade away” for decades. But that mindset is becoming a liability.
Credible sources—including NIST, NSA, and prominent research institutions—now anticipate that cryptographically relevant quantum computers could emerge within the next five years. In the meantime, sophisticated attackers, including nation-state actors, are actively funding a chilling strategy: Harvest Now, Decrypt Later (HNDL): intercepting encrypted communications today—not to break them now, but to store and decrypt them once quantum computers become powerful enough. This isn’t speculation; it’s an active intelligence concern, especially in sectors like finance, defense, and healthcare.
When it hits, the shift will be disruptive. Organizations without a plan will feel the impact all at once. Encrypted backups, secure comms, VPN tunnels, intellectual property—when quantum algorithms can break encryption, all bets are off. There will be no breach alert, no ransomware splash screen, and the consequences will arrive retroactively, impacting data, identities, and decisions that felt safe years ago.
To put this into perspective, consider that encrypted data over five years old may already be within the sights of quantum-capable adversaries. That’s why a reactive stance won’t cut it. In Part 1, we break down the risks, the timeline, and the stakes, so you can start thinking strategically—not someday.

Today’s encryption faces extinction in the post-quantum era
It all starts with the qubit. What sounds like a lesser Pokémon is actually the fundamental building block of quantum computing. If traditional computing is a regular coin with 0 on one side and 1 on the other, qubits allow that coin to spin in the air indefinitely, existing in multiple states at once. This “both/and” magic lets quantum systems evaluate many possible solutions simultaneously. Understandably, this is revolutionary for science, but terrible for encryption.
When quantum systems mature, algorithms will quickly dismantle the asymmetric cryptography we depend on every day. This means that RSA encryption, Elliptical Curve Cryptography (ECC), and Diffie-Hellman (DH) key exchange—the cryptographic backbone of Transport Layer Security (TLS), SSH (Secure Shell), code signing, and every padlock icon in your browser—are at risk.
Quantum computers capable of breaking RSA-2048 don’t exist yet. Building one is a significant challenge. Qubits are notoriously delicate. They decohere easily due to noise and temperature. It takes thousands of physical qubits to create a single reliable logical one. But adversaries don’t need to wait for qubits to be production-ready. They’re playing the long game—recording encrypted data today to decrypt later.
This HNDL model appears to be already active. It targets government communications, intellectual property, medical and financial records, human and machine credentials, and identity tokens—any data with strategic, personal, or economic value.
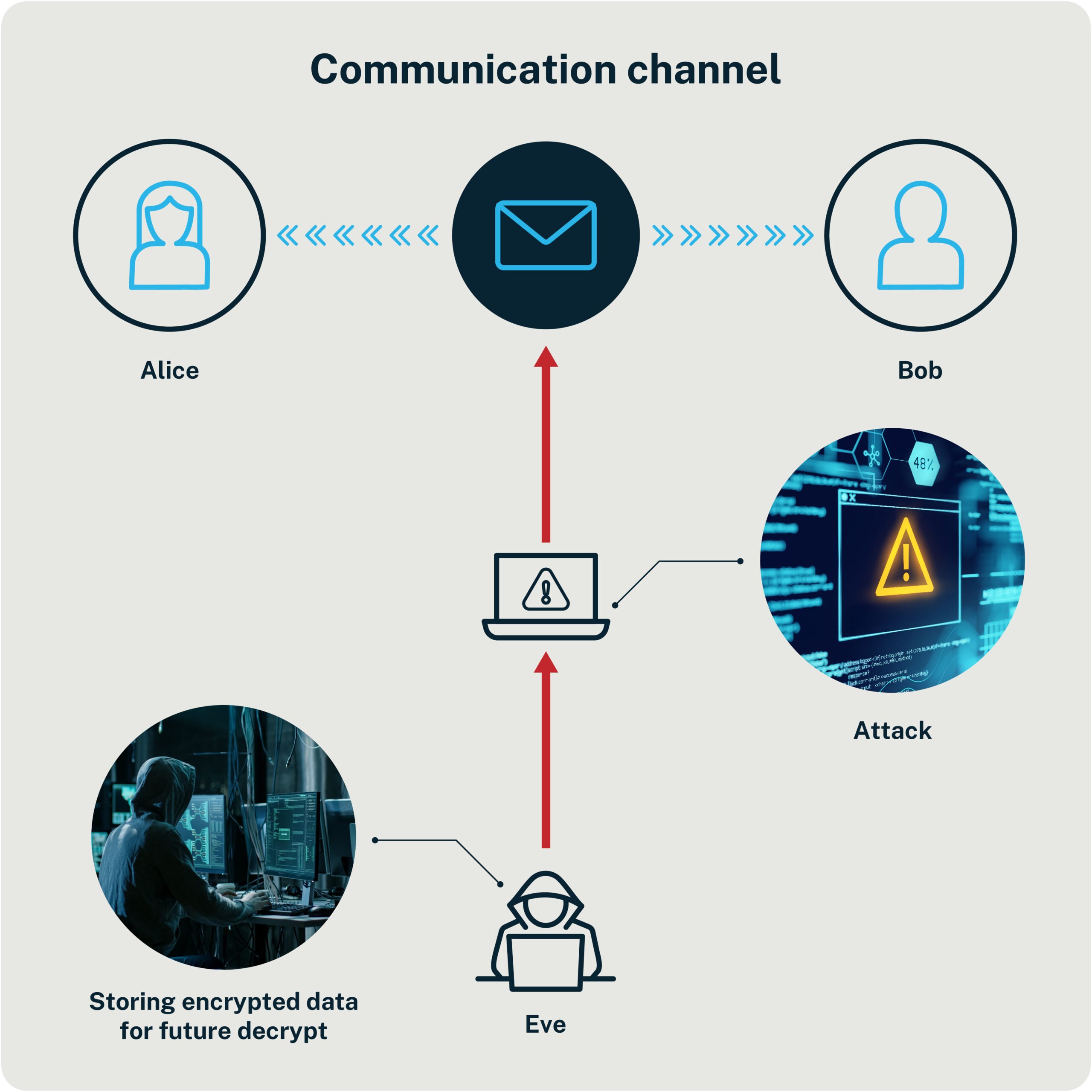
Figure 1. Attackers are already recording encrypted web traffic.
Targets include everything from classified government files to sensitive financials, medical records, and identity tokens — basically anything you wouldn’t want exposed on the dark web yard sale five years from now. If it has long-term value, it’s being hoarded.
Right now, your secrets are still safe—for now. But if your encryption scheme isn’t post-quantum ready, your data is essentially sitting in a well-sealed time capsule with a countdown.
Quantum-capable attackers will have the power to break the cryptographic proofs that secure identities, exposing human and machine credentials. With enough power, they could spoof human or machine identities and compromise protocols we depend on daily: TLS, Security Assertion Markup Language (SAML), remote desk protocol (RDP), SSH. The potential for widespread disruption isn’t just destructive; it’s existential.
Procrastination isn’t post-quantum safe: start your PQC transition now
PQC refers to new cryptographic algorithms resistant to threats posed by quantum computers. These tools are advancing rapidly. In August 2024, the post-quantum future got its own paperwork: the National Institute of Standards and Technology (NIST) promoted three PQC algorithms that vendors are already beginning to integrate into products. Meanwhile, as organizations assess their readiness, regulators are starting to sniff around.
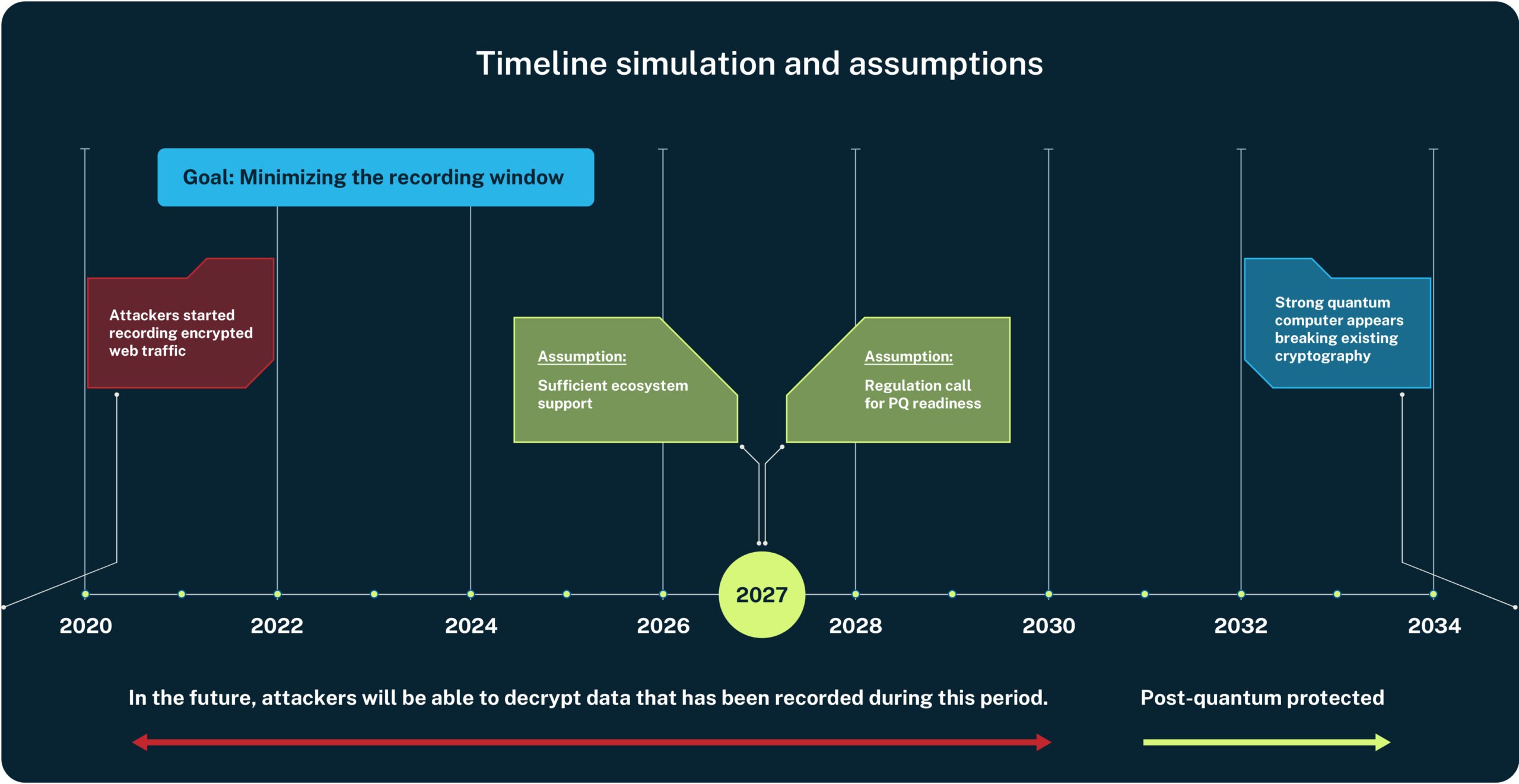
Figure 2. Quantum-enabled adversaries can record encrypted traffic today to decrypt it when quantum computers mature.
Transitioning to quantum-safe cryptography is not a weekend upgrade. It requires a multi-year, multi-phase journey that includes cryptographic inventory, system architecture updates, vendor coordination, and operational changes.
These systems, particularly those governing machine identities, are now foundational to modern Zero Trust architectures and represent some of the most exposed assets in a post-quantum world. Organizations advancing digital transformation, Zero Trust initiatives, or modernizing identity frameworks must integrate PQC readiness into these efforts—not as an afterthought, but as a key pillar.
How to start your post-quantum cryptography transition
What practical ways can you start building PQC readiness across your organization and embed it into your broader machine identity and certificate lifecycle strategy?
Glad you asked. In Part 2, we’ll outline practical steps you can implement today to operationalize PQC without derailing critical infrastructure or digital transformation efforts.
Want the whole picture? If you’re leading the charge on quantum readiness, CyberArk’s new book, “The Identity Security Imperative: A Leader’s Guide to Securing Every Identity,” can help connect the dots between quantum computing, identity security, and executive strategy.
Nick Curcuru is a product marketing director at CyberArk.